Jitterbit Harmony security and architecture white paper
Overview
Jitterbit Harmony is a unified AI-infused low-code platform for integration, orchestration, automation, and app development.
A high-level overview diagram of the Harmony platform depicts its four layers:
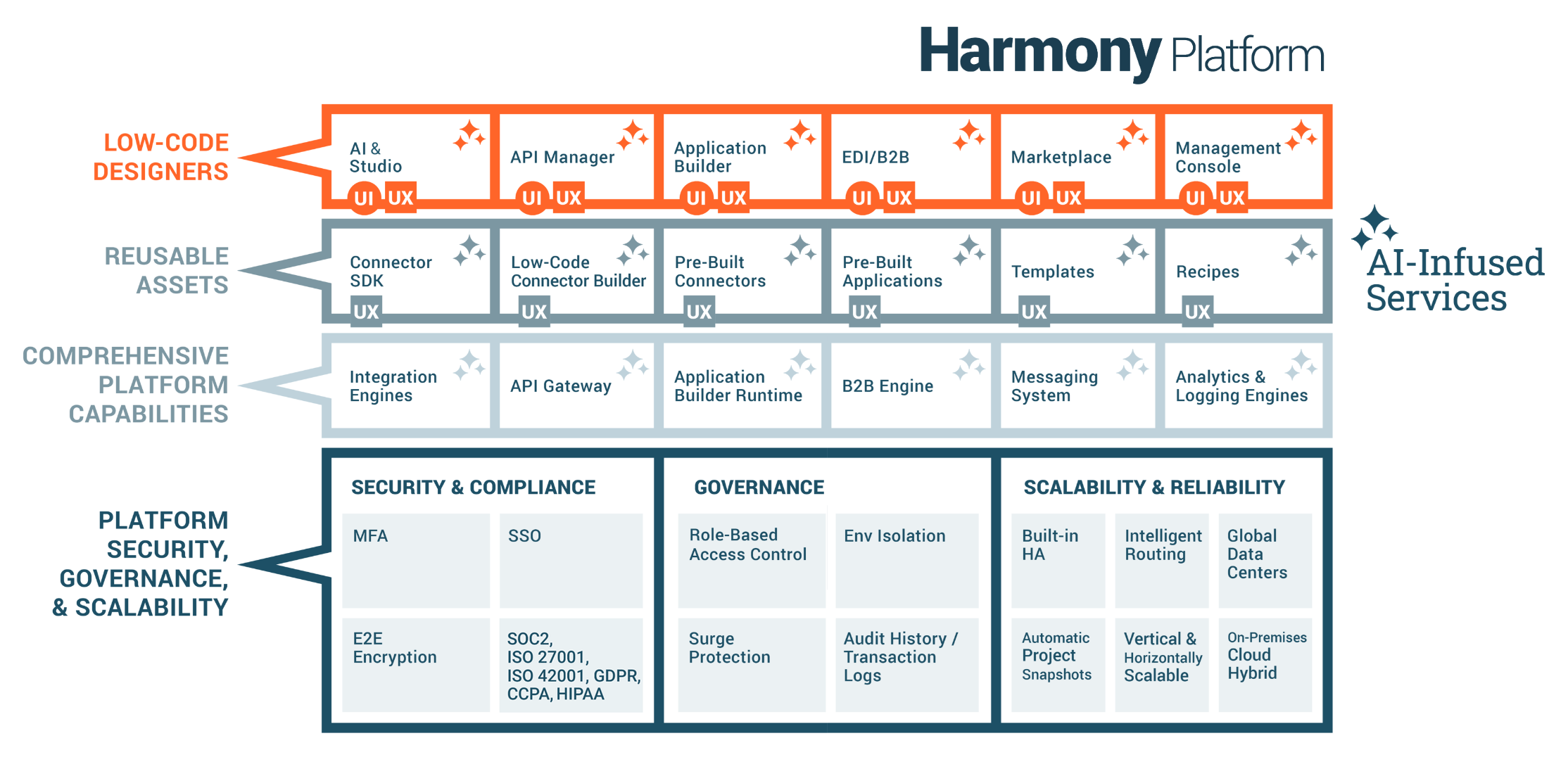
-
Low-code designers provide an intuitive, responsive user interface that is accessible to both technical and non-technical users:
- Studio: Build, manage, and maintain integrations.
- API Manager: Create, control, and consume APIs.
- App Builder: Build, manage, and maintain web and mobile applications.
- EDI: Build, manage, and monitor the exchange of business documents.
- Marketplace: Get certified pre-built integrations.
- Management Console: Manage, monitor, and administer projects in one place.
-
Reusable assets provide a dynamic and seamless user experience. Jitterbit provides pre-built assets for the most common use cases and multiple ways to create your own connectors.
-
Platform engines include the running, monitoring, and reporting of integrations, applications, APIs, and B2B transactions.
-
Enterprise-grade platform security and compliance, governance, and scalability and reliability serve as a foundation for the platform.
The designers, assets, and platform capabilities are infused with AI services that speed up automation, integration, and app development to streamline your business processes.
Jitterbit manages the information security of the Harmony platform by applying a hybrid information security framework based on NIST, CIS, CSA, and CERT recommendations:
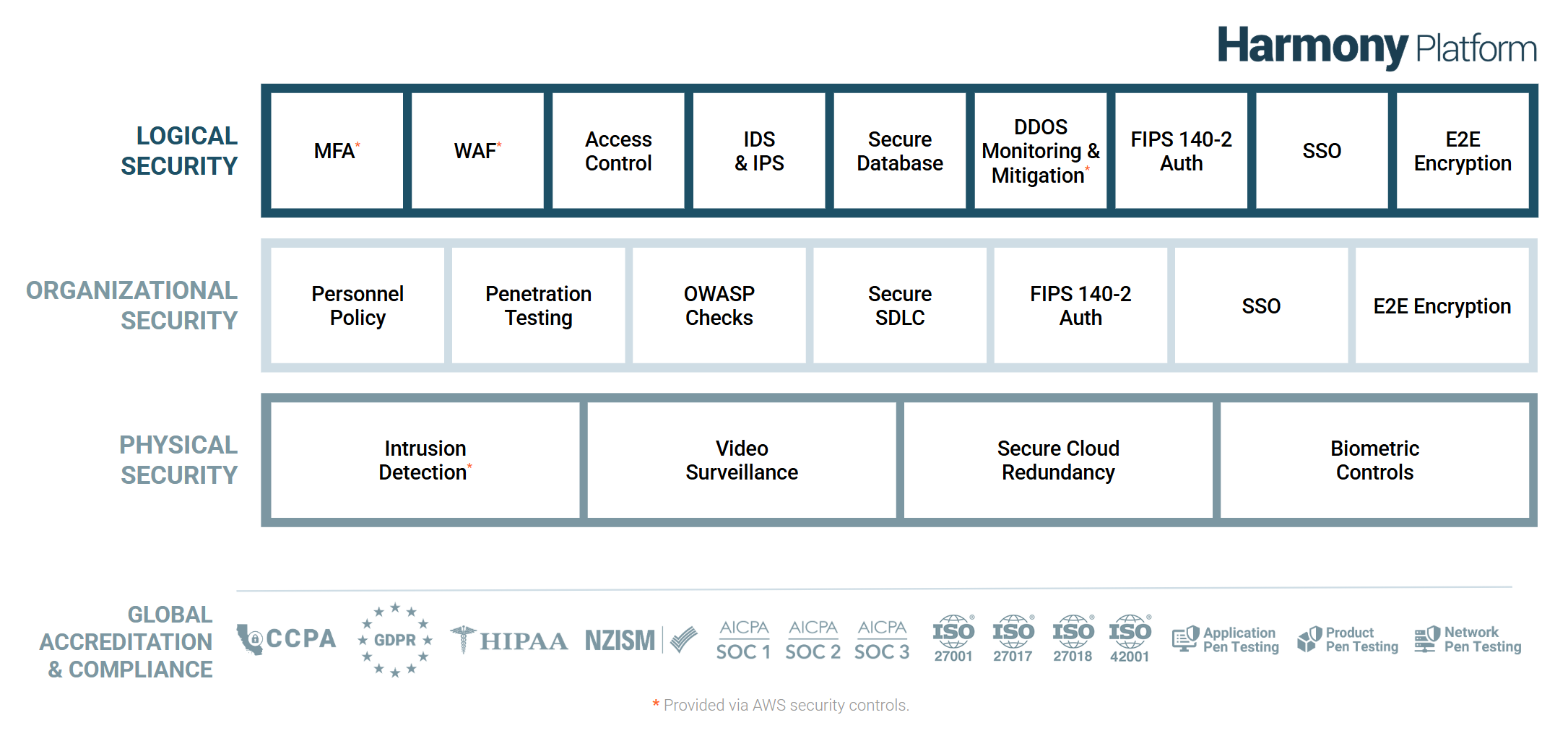
The logical, organizational, and physical security of the Harmony platform are detailed in the remainder of this white paper.
Harmony has also been certified to be compliant with or accredited by these global standards:
- California Consumer Privacy Act (CCPA)
- European Union - General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- New Zealand Information Security Manual (NZISM)
- AICPA SOC 1, SOC 2, and SOC 3 Type 2 compliance
- ISO 27001:2022 with supplemental controls for 27017 and 27018
- ISO 42001:2023 AI certification
The results of penetration testing and additional information about Jitterbit's compliance with security standards is available through our self-service Security Center.
This document takes a broad view of security and covers things to consider from the perspective of availability and performance, in addition to data protection.
Note
This white paper is provided for informational purposes only. It does not cover all local regulations and does not constitute legal advice.