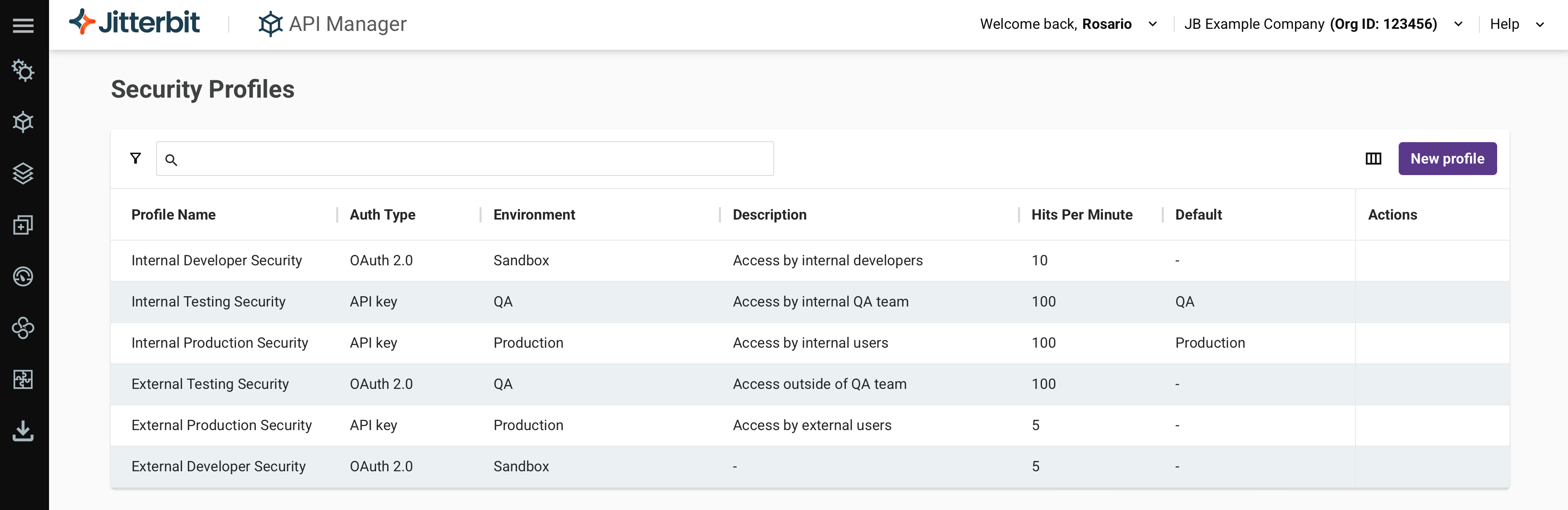
Security Profiles page in Jitterbit API Manager
Introduction
The Security Profiles page in API Manager provides a user interface to configure and manage security profiles. These profiles control and secure how users access API Manager APIs.
To perform actions or make edits on the Security Profiles page, a role with Admin permission is required. Users in non-admin roles with Read or higher environment access have read-only access.
For information about security profiles, see Security profiles in Key concepts.
Access the Security Profiles page
To access the Security Profiles page, use the Harmony portal menu to select API Manager > Security Profiles.
Security Profiles page header
The header at the top of the Security Profiles page includes a search box, filters, and a button for creating a new security profile:
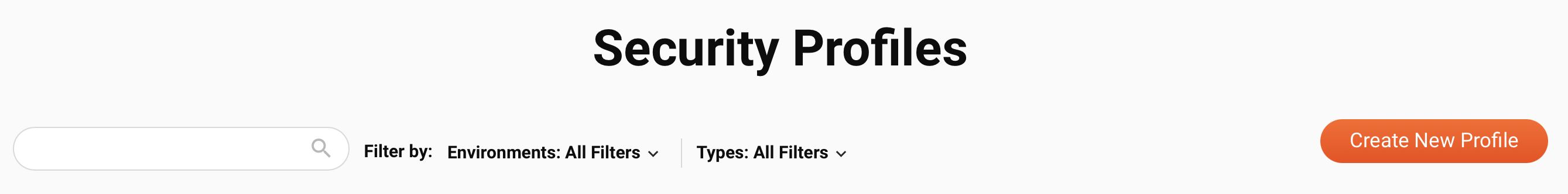
-
Filters: You can filter security profiles by any of the following options:
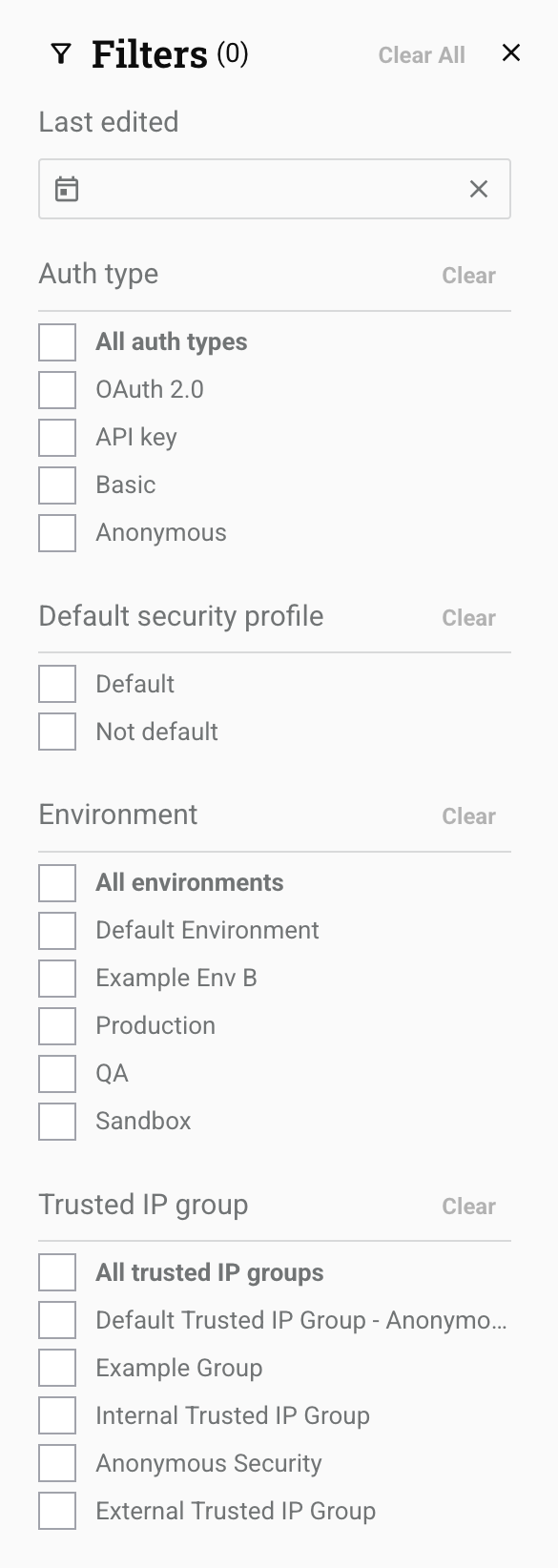
-
Auth type: Select the authentication types for the security profiles. Options include OAuth 2.0, API Key, Basic, or Anonymous. When all filters are unselected, security profiles with any authentication type appear.
-
Default security profile: Select whether to show default or non-default profiles.
-
Environment: Select environments where the security profiles are located. When all filters are unselected, security profiles for all environments in your organization appear (limited to environments you can access).
-
Trusted IP group: Select the trusted IP groups included in the security profiles.
-
-
Search: Enter any part of a security profile's name to filter security profiles by name. The search is not case-sensitive.
-
Filter columns: Click to change the arrangement and visibility of columns. The Columns drawer opens:
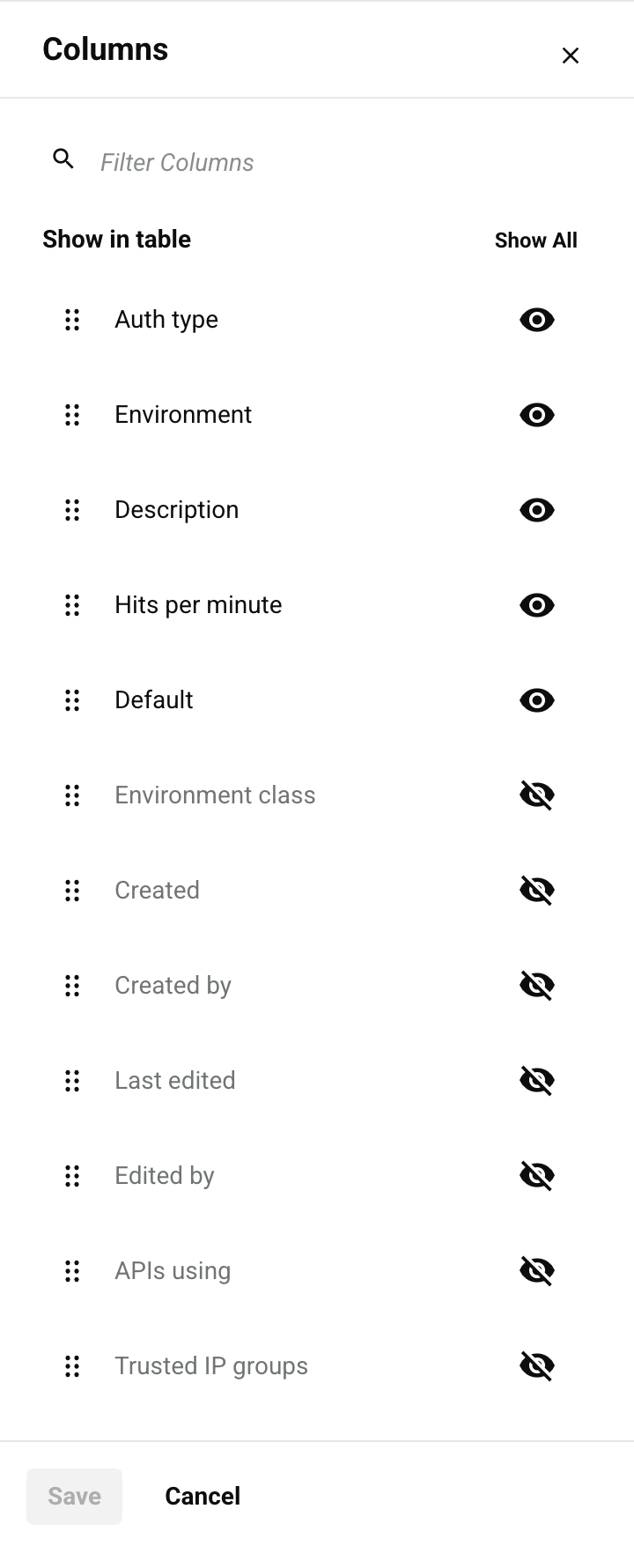
The drawer includes these controls:
- Show All: Make all columns visible.
- Move: Drag and drop to change the column position relative to others.
- Hide: The column is visible. Click to hide it.
- Show: The column is hidden. Click to show it.
- Save: Save the column changes.
- Cancel: Close the columns drawer without saving changes.
-
New profile: Click to open the security profile configuration drawer. Here you can create a new security profile.
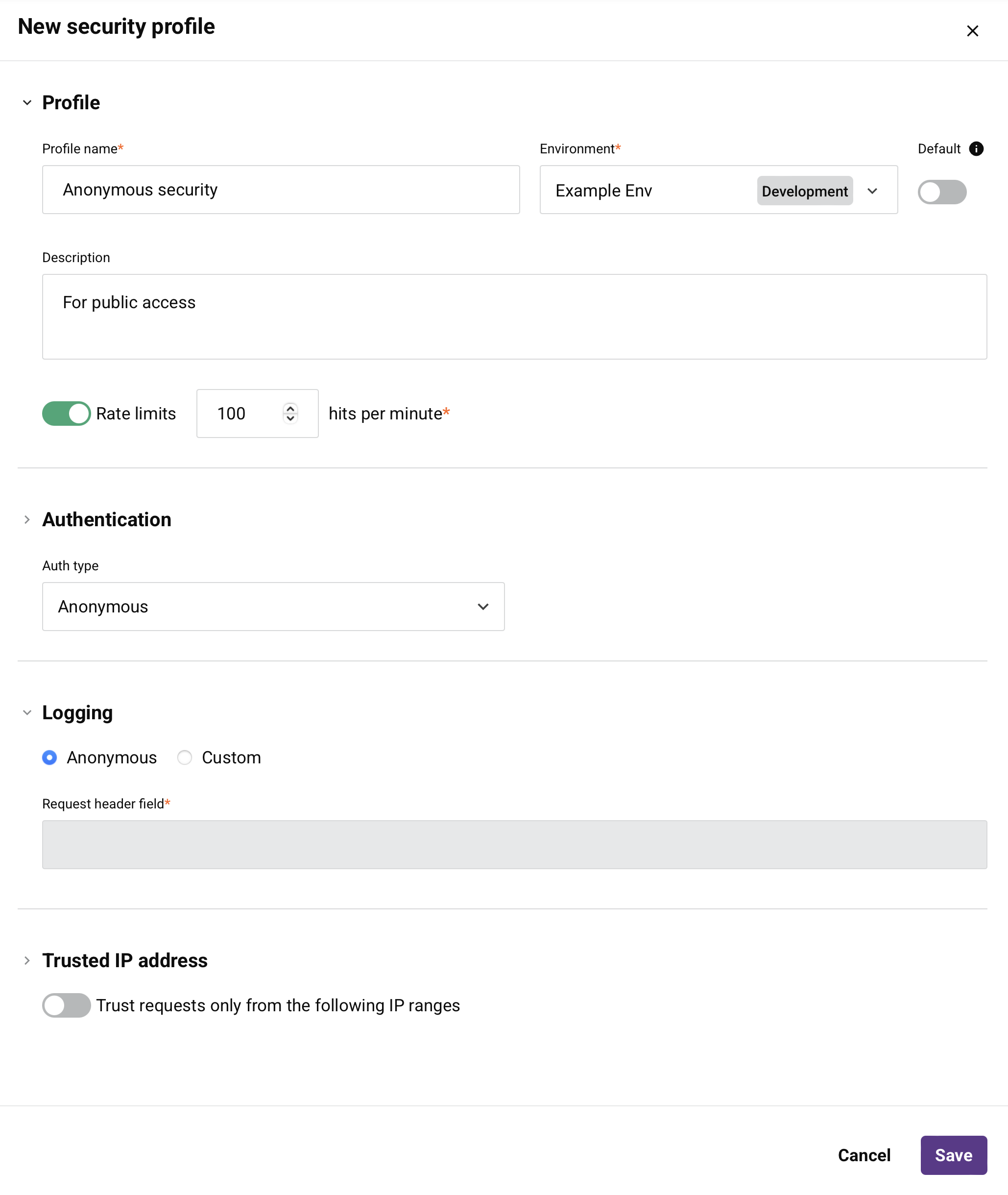
Configure a security profile
The security profile configuration drawer includes these fields and actions:
-
Profile name: Enter a name to identify the security profile. The name must not start or end with a space.
Caution
If you configure the security profile with OAuth 2.0 and use Microsoft Entra ID or Google as the OAuth 2.0 identity provider (configured below), the Profile name must not contain any spaces. If the Profile name contains spaces, you will get an error when you try to access an API to which the security profile is assigned.
-
Environment: Use the dropdown to select an existing environment where the security profile can be assigned. You can type any part of the environment name into the menu to filter the list of environments. The menu results are filtered in real time with each keystroke. To learn more about the relationship of environments to security profiles, see Multiple security profiles in Key concepts.
-
Default: Select to make this security profile the default for the selected environment. The default security profile will be preselected when a new API is created. Only one default security profile can be selected in each environment. After a default security profile has been specified for an environment, selecting a different security profile as the default will replace the existing default security profile selection. Selecting or changing the default security profile will not affect the security profile assigned to existing APIs.
-
Description: Enter an optional description of the security profile.
-
Rate limits and hits per minute: Enable Rate limits to enforce a shared maximum number of API hits per minute that can be made across all APIs to which this security profile is assigned. When this option is selected, you must enter a maximum number of hits per minute.
When enabled, calls over the set maximum are rejected. As such, calls to APIs assigned this security profile may experience an increased number of rejects. For more information, see Rate limits in Key concepts.
-
Auth type: Select an authentication type for the security profile. See Authentication types below for details.
-
Logging: Select the identifier that will be included in API request headers to track which authorization method was used to access this security profile. This value appears in the User set to field in API logs for each API request, allowing you to monitor and audit different access methods.
The label of the first radio button corresponds with the authentication Type configured for the security profile:
-
Anonymous: Sends the value Anonymous.
-
Basic: Sends the value of the Username field (as defined in Basic authentication).
-
OAuth: Sends the value OAuth2.0.
-
API Key: Sends the value APIKEY.
When Custom is selected for Logging, this field becomes available:
- Request header field: Sends the value entered in the text box, for example,
X-API-Key.
-
-
Trusted IP address: Select whether to limit access to the APIs within the security profile to consumers from a single IP address or a range of IP addresses. See Trusted IP addresses below for details.
-
Save: Click to save and close the security profile configuration.
-
Cancel: Click to close the configuration without saving.
Authentication types
After you use the Auth type menu to select the authentication type, additional fields become available to configure. This section describes the fields for each type:
Anonymous
Select the Anonymous authentication type if no authentication is required.
Note
If you do not assign a security profile to an API, then anonymous authentication is also used. However, you might want to use an anonymous security profile (rather than no security profile) to be able to set additional security options for Logging, Trusted IP Ranges, or Rate Limits, as described in Configure a security profile.
API key
Select the API Key authentication type to use an API key and value pair to access an API assigned this security profile. When this type is selected, these fields are used to create the required credentials:
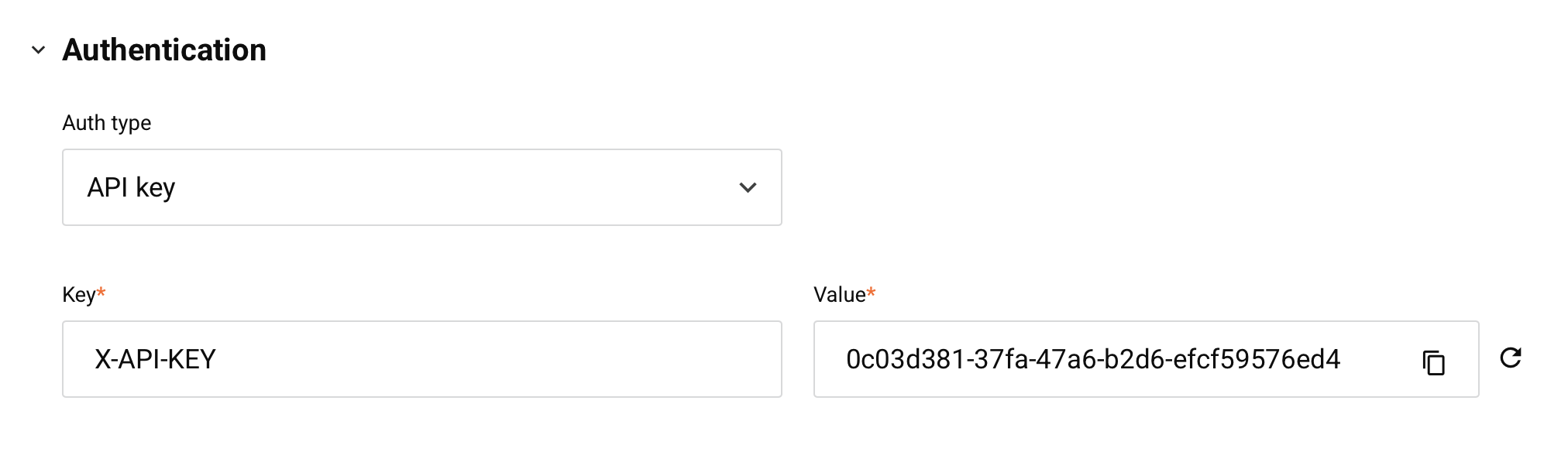
- Key: Enter the header name that you want to use, such as Authorization or X-API-KEY. A maximum of 256 characters is allowed.
- Value: A value is automatically generated for use with the Key header name. You can edit the value or use the refresh icon to generate a new value. A maximum of 256 characters is allowed.
- Copy: Copies the Value to your clipboard.
Note
The key and value pair that is entered is accepted both as a header and as a query parameter. For example, a Key of X-API-KEY with a Value of abc123 is passed in a header as X-API-KEY:abc123 and in a query parameter as ?X-API-KEY=abc123.
Basic
Select the Basic authentication type to use basic HTTP authentication to access an API assigned this security profile. When this type is selected, these fields are used to create the required credentials:
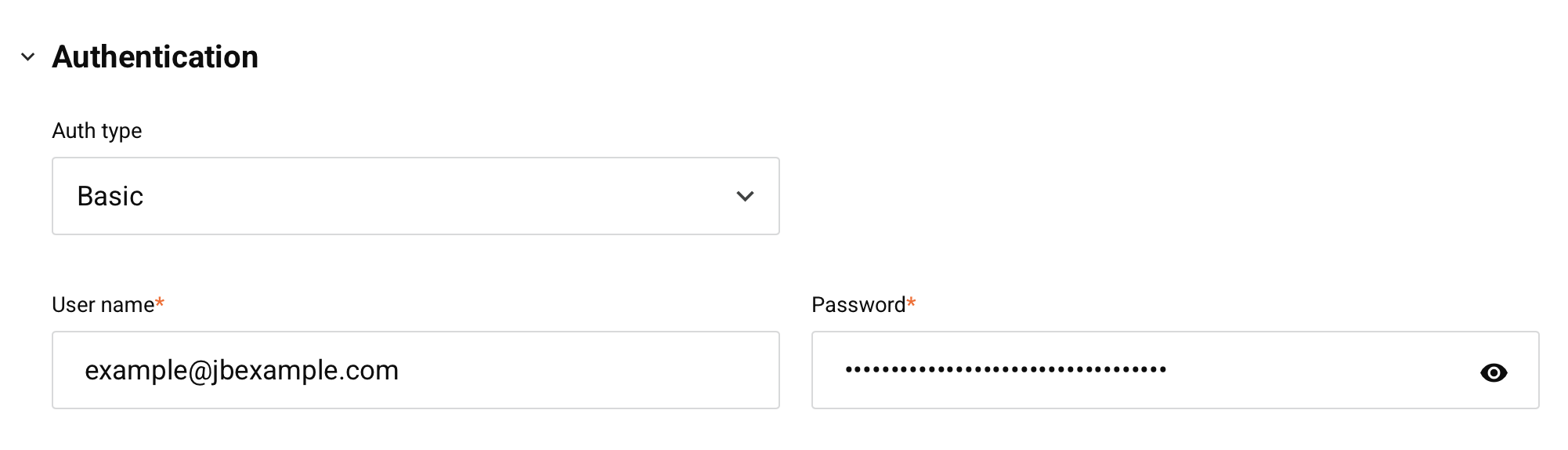
-
Username: Enter a username to create for accessing the API. The username is case-sensitive and should not contain a colon (
:) if you intend to use the credentials in an HTTP header when calling the API. -
Password: Enter a password to create for accessing the API.
Tip
To use the credentials in an HTTP header when calling an API assigned this security profile, provide a Base64-encoded string of the username and password combined with a single colon. For example, using the Jitterbit function Base64Encode:
Base64Encode("exampleuser"+":"+"examplepassword")
OAuth 2.0
Select the OAuth 2.0 authentication type to use an OAuth 2.0 authorization token to access an API assigned this security profile. OAuth 2.0 is an open standard for access delegation. When this type is selected, these fields are used to create the required credentials:
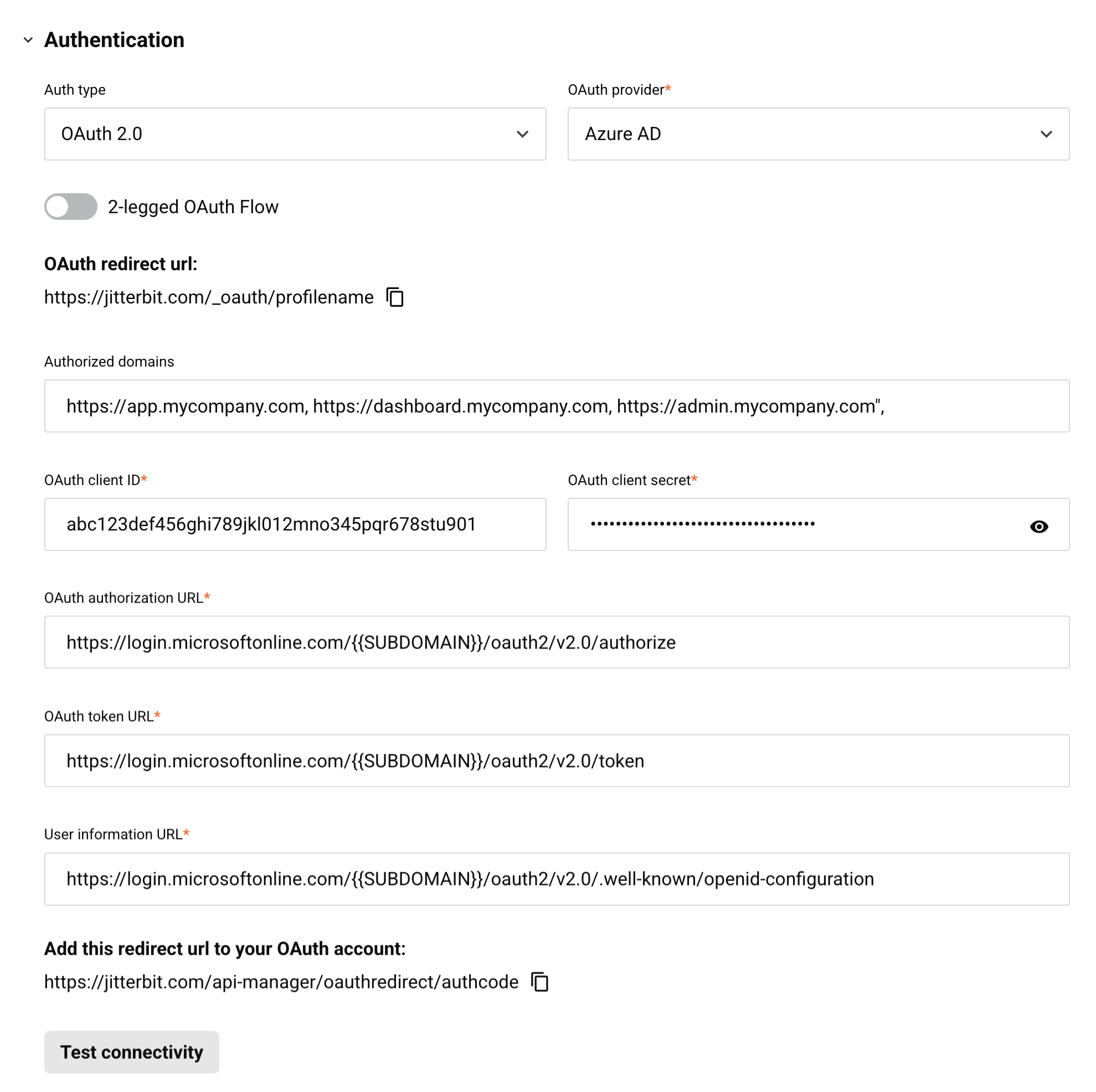
-
OAuth provider: Use the dropdown to select a supported identity provider. Choose one of Azure AD (Microsoft Entra ID), Google, Okta, or Salesforce.
-
OAuth redirect URL: This field is prepopulated and cannot be edited. This value is required as input when you get the client ID and client secret for Microsoft Entra ID, Google, Okta, or Salesforce.
-
2-legged OAuth Flow: By default, 3-legged OAuth is used for all identity providers. This process requires manual interaction to authenticate when accessing an API assigned this security profile. The 2-legged OAuth Flow option is available only for Microsoft Entra ID (Microsoft Entra ID) and Okta. This option lets you configure a scope and an audience to remove the manual step.
Note
If you use a private API gateway, you must use gateway version 10.48 or later for this option to work. If the gateway is not version 10.48 or later, 3-legged OAuth is used even if 2-legged OAuth is configured. If you are not using a private API gateway, this option has no version requirements.
-
OAuth scope: (Visible only when 2-legged OAuth Flow is enabled.) Enter the scope to be used for 2-legged OAuth. Refer to the instructions for Microsoft Entra ID (Microsoft Entra ID) or Okta.
-
Authorized domains: Enter domain names separated by commas to limit access to allowlisted domains. Leave blank for unrestricted access.
-
OAuth client ID and OAuth client secret: Enter the client ID and client secret that you got from the identity provider. Refer to instructions for getting the client ID and client secret for Microsoft Entra ID, Google, Okta, or Salesforce.
-
OpenID discovery URL: (Visible only when 2-legged OAuth Flow is enabled.) This field is prepopulated with standard default values from the identity provider. These values must be edited with values that are specific to the Microsoft Entra ID or Okta instance. Refer to instructions for Microsoft Entra ID (Microsoft Entra ID) or Okta.
-
Audience: (Visible only when 2-legged OAuth Flow is enabled.) Enter the audience to be used for 2-legged OAuth. Refer to the instructions for Microsoft Entra ID or Okta.
-
OAuth authorization URL, OAuth token URL, and User info URL: These fields are prepopulated with standard default values from the identity provider. They might need to be edited depending on the identity provider:
-
Google or Salesforce: Normally, these values should not need to be edited. If you are using a custom implementation and need to override the default values, you can edit them here. For more help, contact Jitterbit support.
-
Azure AD or Okta: These values must be edited with values that are specific to the Microsoft Entra ID or Okta instance. Refer to instructions for Microsoft Entra ID or Okta.
-
-
Add this redirect URL to your OAuth account: This field is prepopulated and cannot be edited. This value is required as input when you get the client ID and client secret for Microsoft Entra ID, Google, Okta, or Salesforce.
-
Test connectivity: Click to verify connectivity with the identity provider using the provided configuration. The resulting behavior depends on whether the 2-legged OAuth Flow option is being used:
-
2-legged OAuth: For Microsoft Entra ID and Okta when 2-legged OAuth Flow is being used, the API gateway gets the access token and authentication happens automatically. You are then redirected to API Manager with a message that shows the results of the test.
-
3-legged OAuth: For Google and Salesforce, and for Microsoft Entra ID and Okta when 2-legged OAuth Flow is not being used, a new browser tab displays the native login interface for the identity provider. After you provide your credentials for the identity provider, you are redirected to API Manager with a message that shows the results of the test.
-
Trusted IP addresses
You can select whether to limit access to the APIs within the security profile to consumers from a single IP address or a range of IP addresses:
-
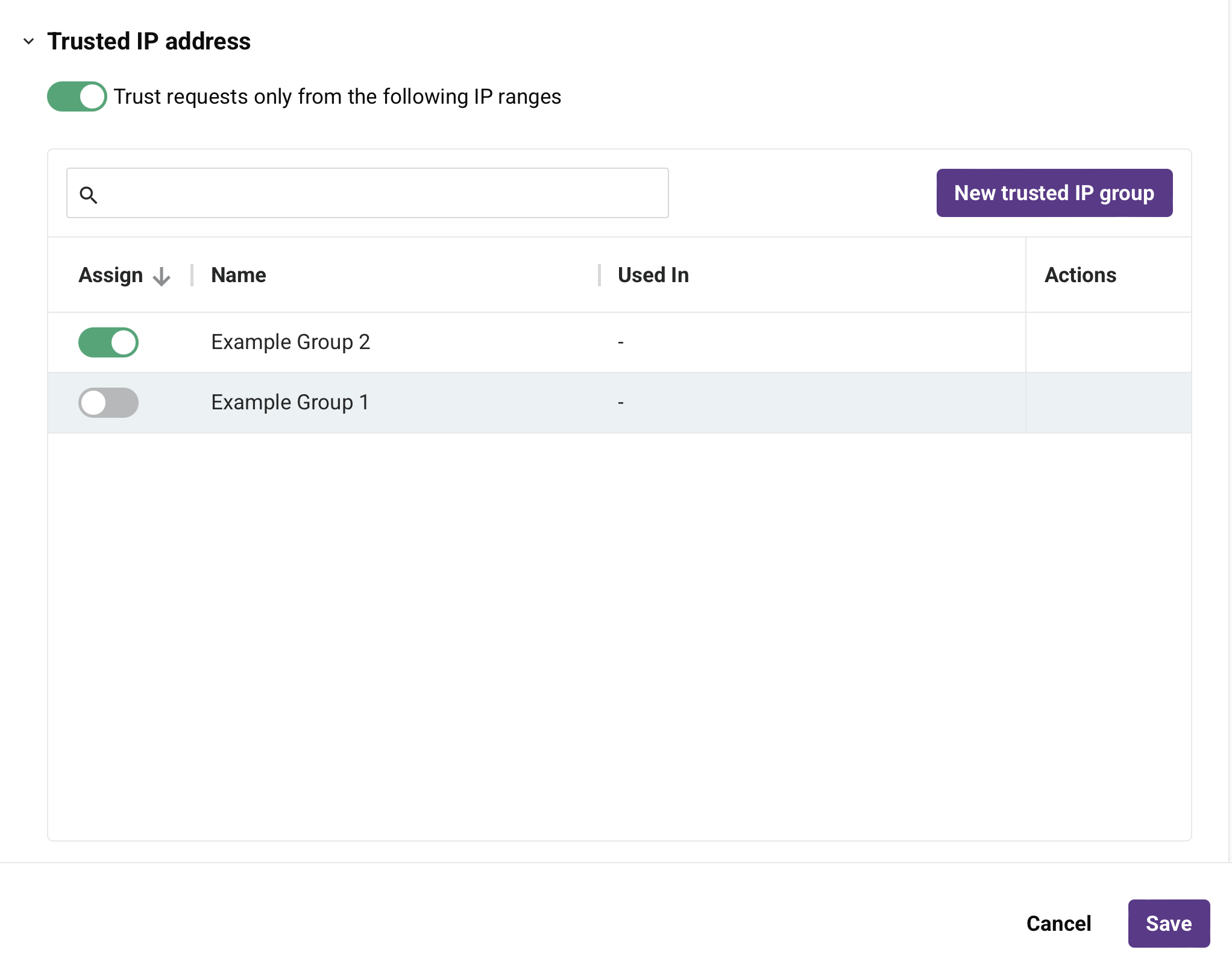
Trust requests only from the following IP ranges: Enable to limit access to the APIs within a security profile to consumers from certain IP addresses. Only IP addresses that are included within the specified ranges can access the APIs using this security profile. When enabled, a table of existing trusted IP groups appears:
-
Search: Enter the name of an existing trusted IP group. When you click the search box, a list of existing trusted IP groups is populated. The list is filtered in real time with each keystroke within the search box. Click the name of the trusted IP group to add it to the security profile.
-
Assign: Enable to assign the trusted IP group to the security profile.
-
Name: The name of the trusted IP group.
-
Used in: The names of the security profiles where the trusted IP group is currently used.
-
Actions: Hover on a trusted IP group row to reveal an additional action:
- Edit: Click to edit the IP ranges for the trusted IP group row.
-
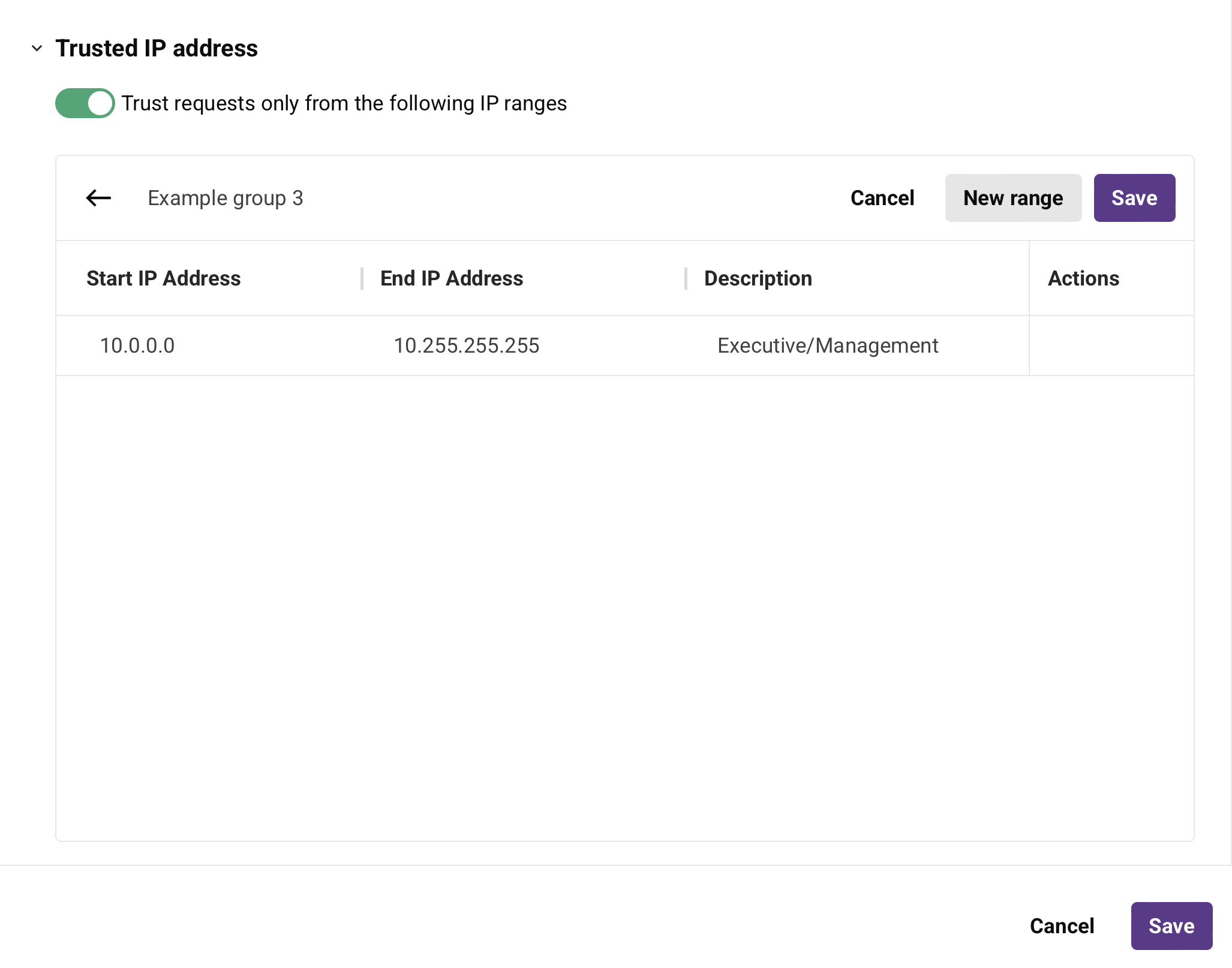
New trusted IP group: Click to add a new trusted IP group. When clicked, this configuration screen is displayed:
-
Name: Enter a name to identify the trusted IP group. For existing trusted IP groups, click the name of a trusted IP group to rename it.
-
New range: Click to add a range of IP addresses.
-
Start IP Address: Enter the first IP address to include in the range. Only IP addresses entered in IPv4 format are supported.
-
End IP Address: Enter the last IP address to include in the range. Only IP addresses entered in IPv4 format are supported.
-
Description: Enter a description of the IP address range (optional).
-
Actions: Hover on an IP address range to reveal an additional action:
- Delete: Deletes the IP address range row from the security profile.
-
Cancel: Click to discard the trusted IP group and return to the security profile configuration.
-
Save: Click to save the trusted IP group. After the security profile has been saved, this trusted IP group will be available for use in other security profiles as needed.
-
-
View existing security profiles
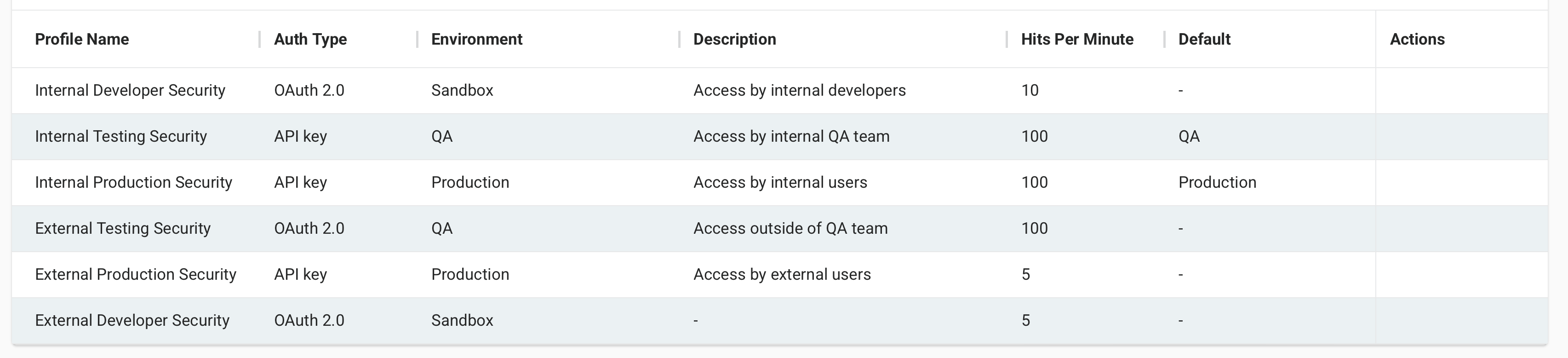
The Security Profiles page displays all existing security profiles in the selected Harmony organization, grouped by environment. Each table column is described below:
-
Profile Name: The name of the security profile. To toggle the sorting order of each table between descending and ascending alphabetical order, click the up or down arrow.
-
Auth Type: The authentication type used to authenticate with and access the APIs assigned to this security profile.
-
Description: A description of the security profile, if provided.
-
APIs using: The APIs the security profile is assigned to.
-
Hits per minute: The maximum number of API requests allowed per minute using this profile, if configured.
-
Environment: The environment where the security profile applies.
-
Environment class: The class of the environment. This information is used for reporting purposes only.
-
Default: The name of the security profile's the default environment, if configured.
-
Created: The date and local browser time when the security profile was created.
-
Created by: The email address of the user who created the security profile.
-
Last edited: The date and local browser time when the security profile was last modified.
-
Edited by: The email address of the user who most recently edited the security profile.
-
Trusted IP groups: Any trusted IP groups assigned to the security profile. For more information, see Trusted IP addresses.
-
Actions: Hover over a security profile to reveal these action icons:
-
Edit: Click to open the security profile configuration screen.
-
Delete: Click to permanently delete the security profile. A message asks you to confirm the deletion. If the security profile is assigned to any APIs, you must first unassign it or replace it before deleting.
Important
After you unassign a security profile from an API, you must save and publish the API for the change to take effect. Until the API is published, the security profile is still considered "in use" and cannot be deleted until all APIs that previously used it have been published with the updated configuration. This applies even if the API is in draft status with the profile unassigned.
-
OAuth display URL: When a 2-legged OAuth security profile is configured, click to copy the URL needed to generate an OAuth token. For instructions, see 2-legged Microsoft Entra ID or 2-legged Okta.
-
Next steps
For more information about assigning security profiles to an API, see these resources: