Configure an identity provider for use with Jitterbit Harmony single sign-on (SSO)
Introduction
Before you can configure SSO, you must set up your identity provider. This page shows how to do this for the following protocols and identity providers:
-
OAuth 2.0
- Autodesk
- BMC (proprietary to BMC customers only)
- Salesforce
-
SAML 2.0
In these sections, the redirect and callback URLs for Harmony clients are as follows:
-
OAuth 2.0
WMChttps://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/oauthStudiohttps://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/oauth/login/studio/callback -
SAML 2.0
WMChttps://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/samlStudiohttps://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml/login/studio/callback
REGION is your Harmony region, one of na-east, emea-west, or apac-southeast.
Changes to redirection URLs
Previously published redirection URLs (containing jitterbit-cloud-mgmt-console) are being updated to the new URLs shown above.
While the old URLs will continue to work through redirection to the new ones, they will be deprecated at some point in the future.
Jitterbit recommends that organizations currently enabled for SSO and using configured identity providers with the old URLs should reconfigure SSO using the new URLs as soon as possible to prevent any future disruptions.
OAuth 2.0
Autodesk
To get an Autodesk OAuth 2.0 client ID and client secret, log in to the Autodesk Forge portal, then follow these steps for two Jitterbit client applications, WMC, for access to the Harmony web applications via the Harmony portal, and Studio, for access to Design Studio:
Important
You must create both apps even if you don't intend to use Design Studio.
-
Go to My Apps and click the Create App button.
-
Set the following values:
-
App Name: Enter the app name that users see when logging in to Harmony via this provider.
-
Callback URL: Enter your Harmony region's OAuth redirect or callback URL for the Jitterbit client application.
-
-
Click Create App.
-
Use the client ID and client secret in the app's section of the Configure SSO OAuth 2.0 drawer on the Management Console Organizations page.
BMC
For instructions on how to configure the BMC identity provider, contact BMC customer support.
To get a Google OAuth 2.0 client ID and client secret, log in to the Google API Console, then follow these steps for two Jitterbit client applications, WMC, for access to the Harmony web applications via the Harmony portal, and Studio, for access to Design Studio:
Important
You must create both apps even if you don't intend to use Design Studio.
-
From the Dashboard, click Create Project.
-
On the New Project screen, enter a Project name.
Tip
You can create both Jitterbit client applications within the same project.
If required, select an Organization and Location, then click Create:
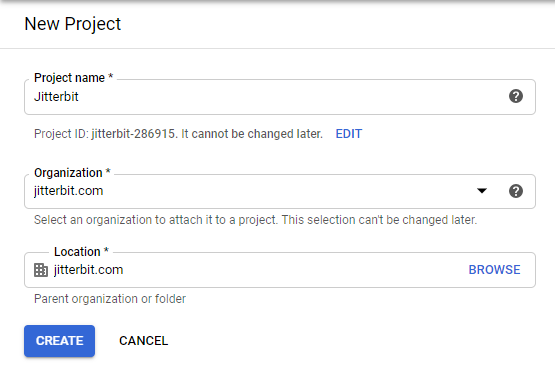
-
Go to the project's OAuth consent screen tab, select External, then click Create:
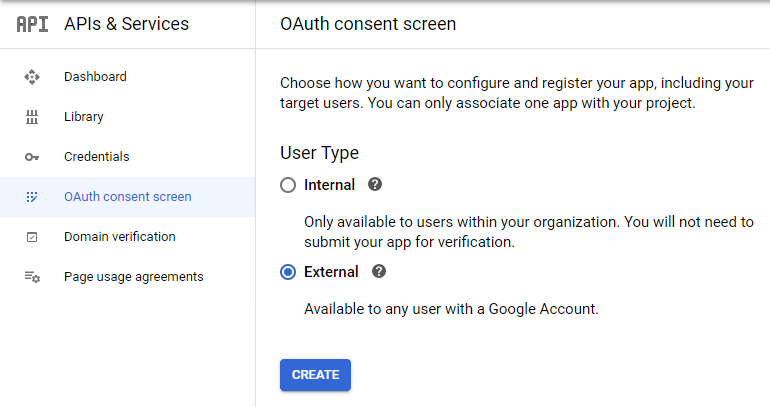
-
In the OAuth consent screen, enter an App name, complete the required contact information, and make any additional changes to the default values.
-
Click Save and Continue.
-
Go to the project's Credentials tab.
-
Click Create Credentials.
-
In the dropdown, select OAuth client ID, then set the following values:
-
Application type: Select Web application.
-
Name: Enter a name for the client.
-
-
Under Authorized redirect URIs, click Add URI, then set the following:
- URIs: Enter your Harmony region's redirect URL for the Jitterbit client application.
-
Click Create.
-
Use the client ID and client secret in the app's section of the Configure SSO OAuth 2.0 drawer on the Management Console Organizations page.
Salesforce
To enable Salesforce as an identity provider and get an OAuth 2.0 client ID and client secret, log in to the Salesforce Classic UI as a Salesforce Admin, then follow these steps:
-
Navigate to Setup > Administer > Security Controls > Identity Provider.
-
In the section Identity Provider Setup, verify that you have a domain name configured and that Salesforce is enabled as an identity provider:
-
If you do not have a domain configured, click the link to Configure a Domain Name and follow the steps to set up a domain and deploy it to users. This automatically enables Salesforce as an identity provider.
-
If you have a domain configured but disabled as an identity provider, click the button Enable Identity Provider.
Tip
After making changes in Identity Provider Setup, you may need to refresh the page.
-
Do the following steps for two Jitterbit client applications, WMC, for access to the Harmony web applications via the Harmony portal, and Studio, for access to Design Studio:
Important
You must create both apps even if you don't intend to use Design Studio.
-
In the Service Providers section, click the link to create via Connected Apps, or navigate to Setup > Build > Create > Apps and click New under the Connected Apps section.
-
Set the following values:
-
Basic Information:
-
Connected App Name: Enter a name for the Jitterbit client application.
-
Set any other required fields.
-
-
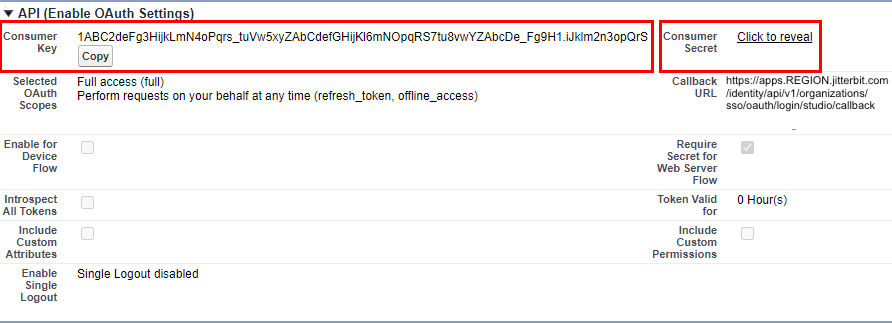
API (Enable OAuth Settings):
-
Enable OAuth Settings: Enable this setting to reveal the Callback URL and Selected OAuth Scopes fields:
For WMC:
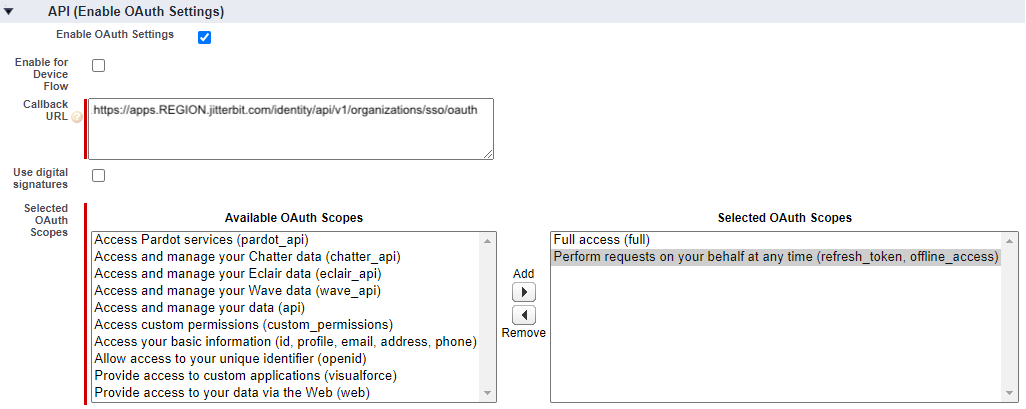
For Studio:
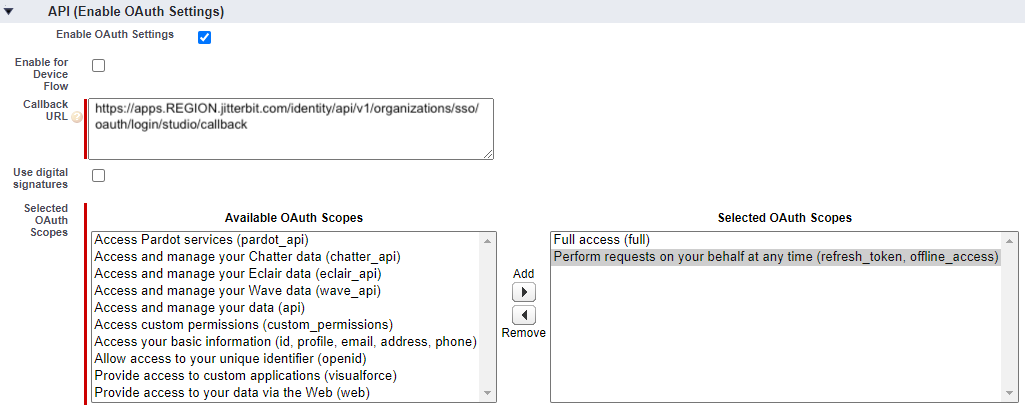
Set these fields as follows:
-
Callback URL: Enter your Harmony region's redirect or callback URL for the Jitterbit client application.
-
Selected OAuth Scopes: Select these OAuth scopes by moving them to Selected OAuth Scopes:
-
Full access (full)
-
Perform requests on your behalf at any time (refresh_token, offline_access)
-
-
-
-
-
Click Save.
-
Under API (Enable OAuth Settings), use the Consumer Key for the client ID and the Consumer Secret for the client secret in the app's section of the Configure SSO OAuth 2.0 drawer on the Management Console Organizations page.
SAML 2.0
Microsoft Entra ID
To get the SAML 2.0 identity and service provider metadata for Microsoft Entra ID (now known as Microsoft Entra ID), log in to the Microsoft Azure portal with an account that includes Microsoft Entra ID P2 edition, then follow these steps:
-
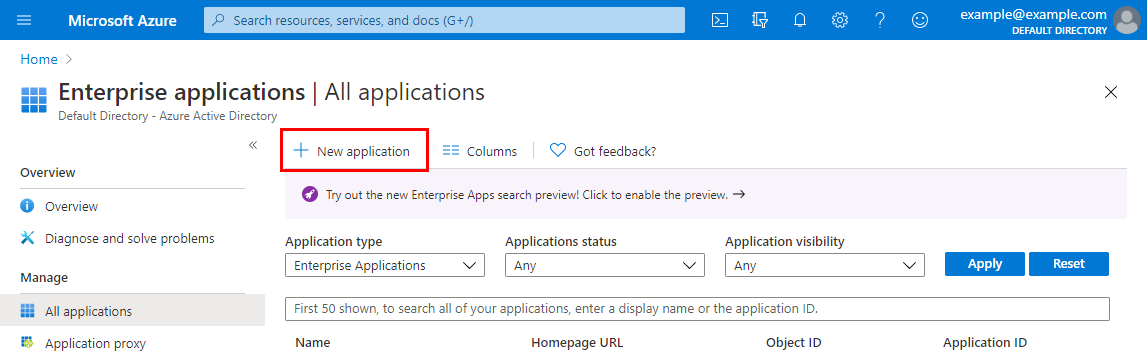
Go to the Enterprise applications blade and click New application:
-
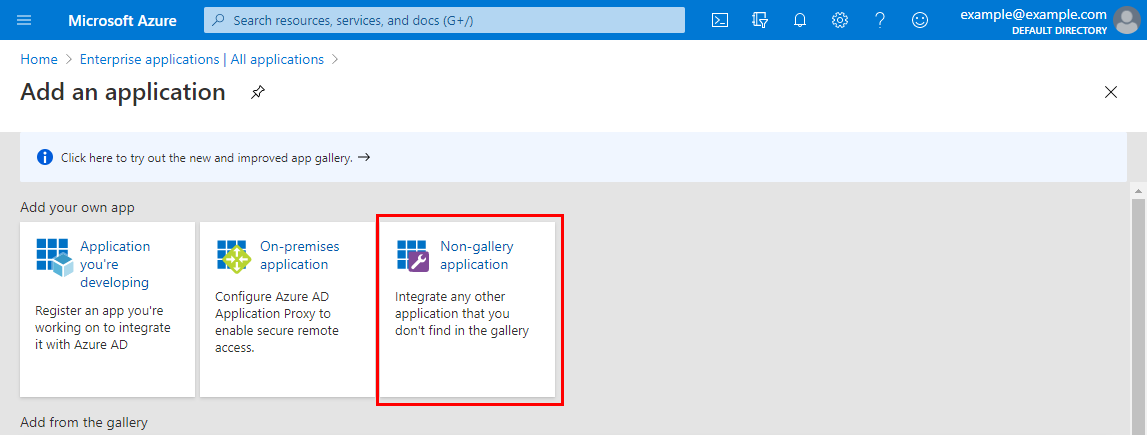
On the Add an application screen under Add your own app, select Non-gallery application:
-
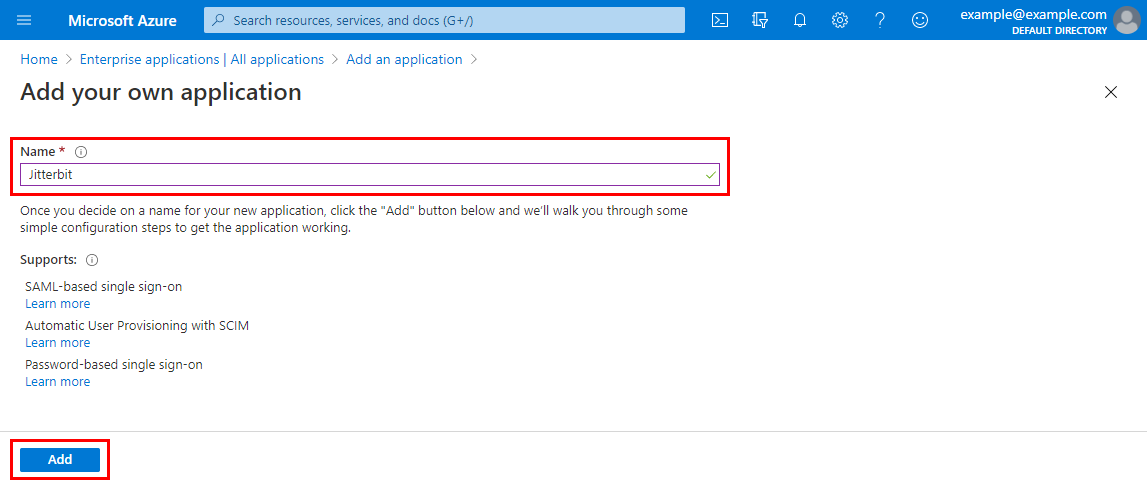
On the Add your own application screen, enter a name for the new application, then click Add:
-
On the Overview screen for the new application, under the Manage category on the left, select Single sign-on:
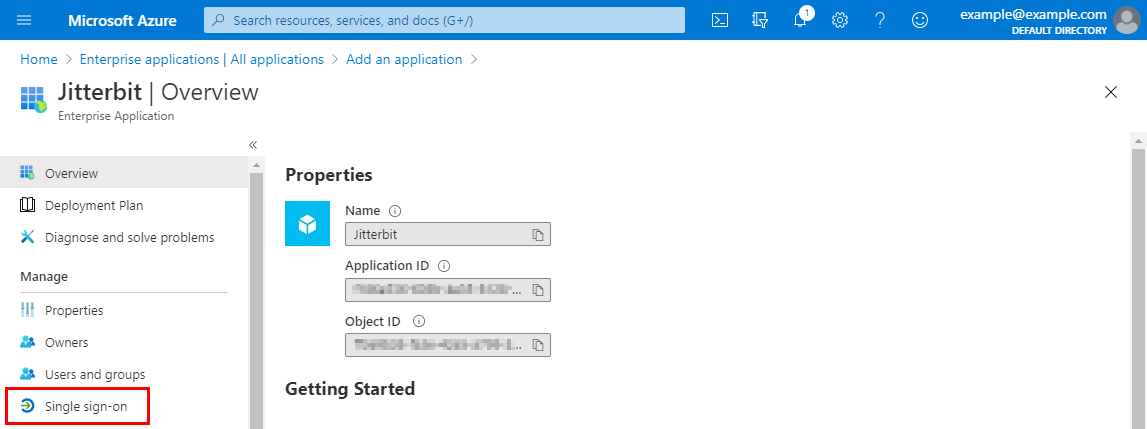
-
On the Single sign-on screen for the new application, under Select a single sign-on method, select SAML:
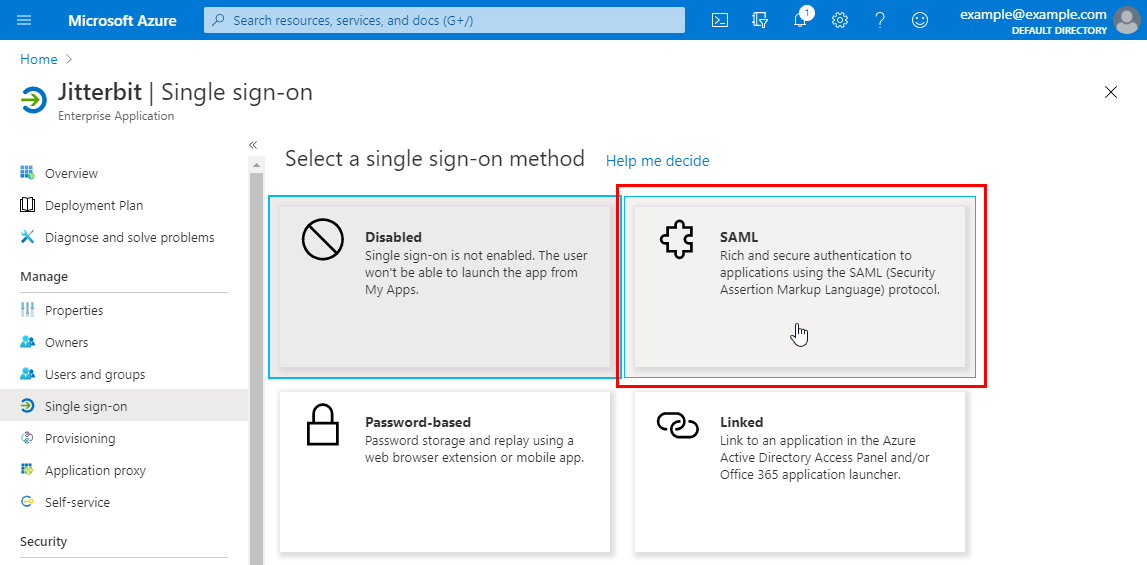
-
On the SAML-based Sign-on screen, edit the first step, Basic SAML Configuration:
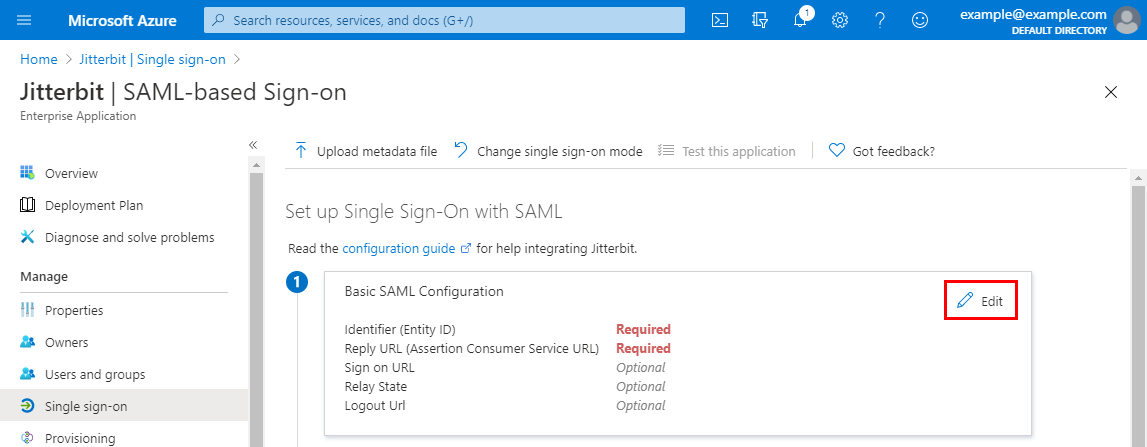
-
On the Basic SAML Configuration screen, set values for the following fields:
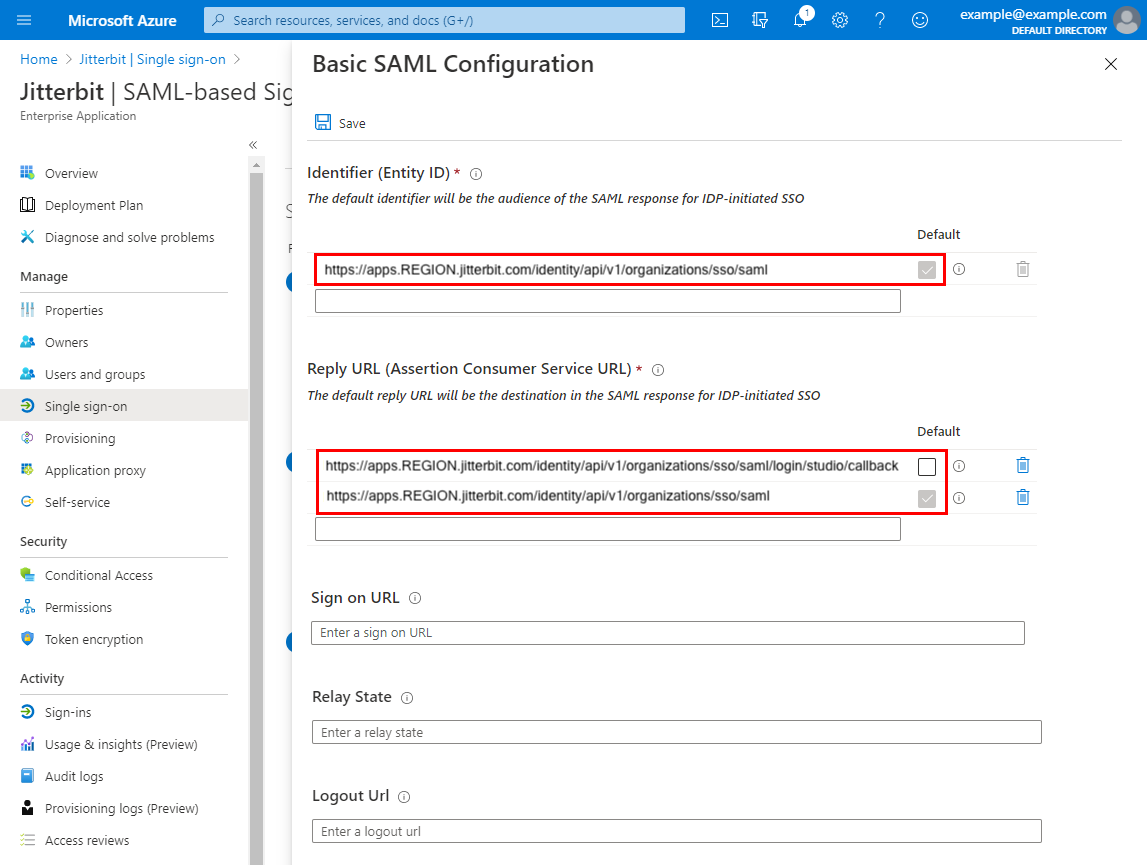
-
Identifier (Entity ID): Enter your Harmony region's SAML redirect URL for the WMC Jitterbit client application, and select the Default checkbox.
-
Reply URL (Assertion Consumer Service URL): On separate lines, enter your Harmony region's SAML redirect and callback URLs for both Jitterbit client applications, WMC, for access to the Harmony web applications via the Harmony portal, and Studio, for access to Design Studio. Select the Default checkbox for the WMC redirect URL.
Important
You must create both apps even if you don't intend to use Design Studio.
-
-
Click Save and close.
-
On the SAML-based Sign-on screen, edit the second step, User Attributes & Claims:
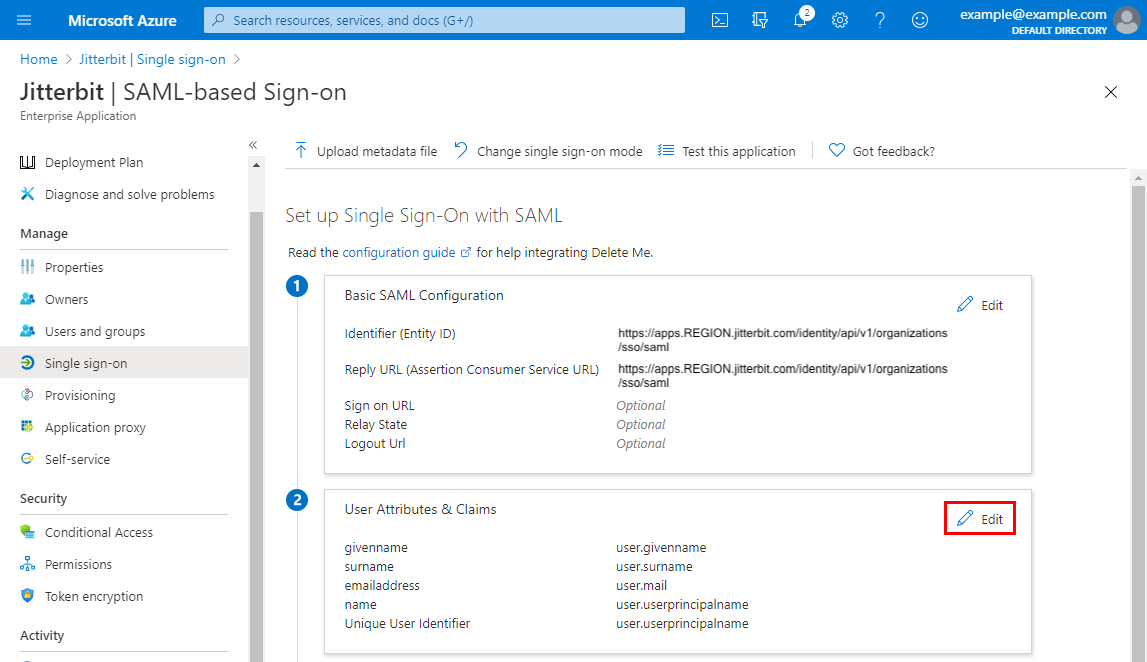
-
By default, Microsoft Azure uses the
user.userprincipalnameas the identifier, which isonemicrosoft.com. This must be changed touser.mail.To open the claim for modifying, click the row with a Claim name of Unique User Identifier (Name ID):
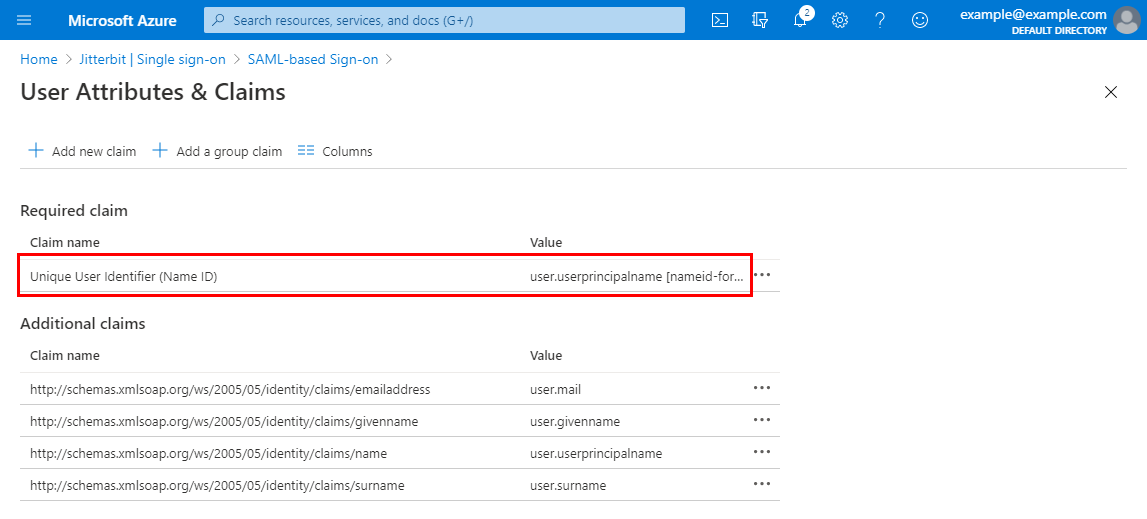
-
On the Manage claim screen, change the Source attribute field from
user.userprincipalnametouser.mail.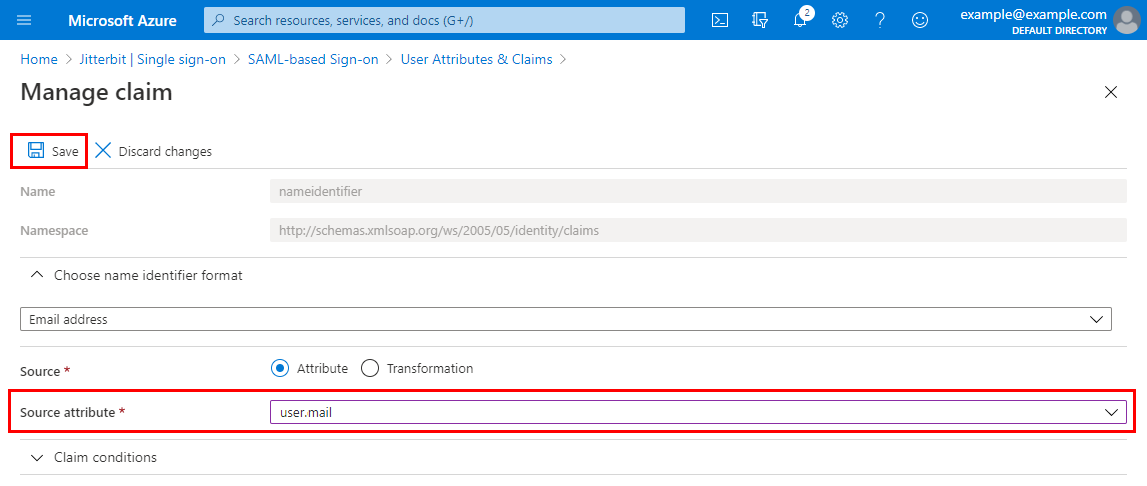
-
Click Save and close.
-
On the SAML-based Sign-on screen, in the third step, SAML Signing Certificate, download the Federation Metadata XML. Use this as the Identity Provider Metadata field in the app's section of the Configure SSO SAML 2.0 drawer on the Management Console Organizations page.
Note
Multiple certificate definitions (
<X509Data>elements) in the metadata are supported with agents version 10.84 / 11.22 and later.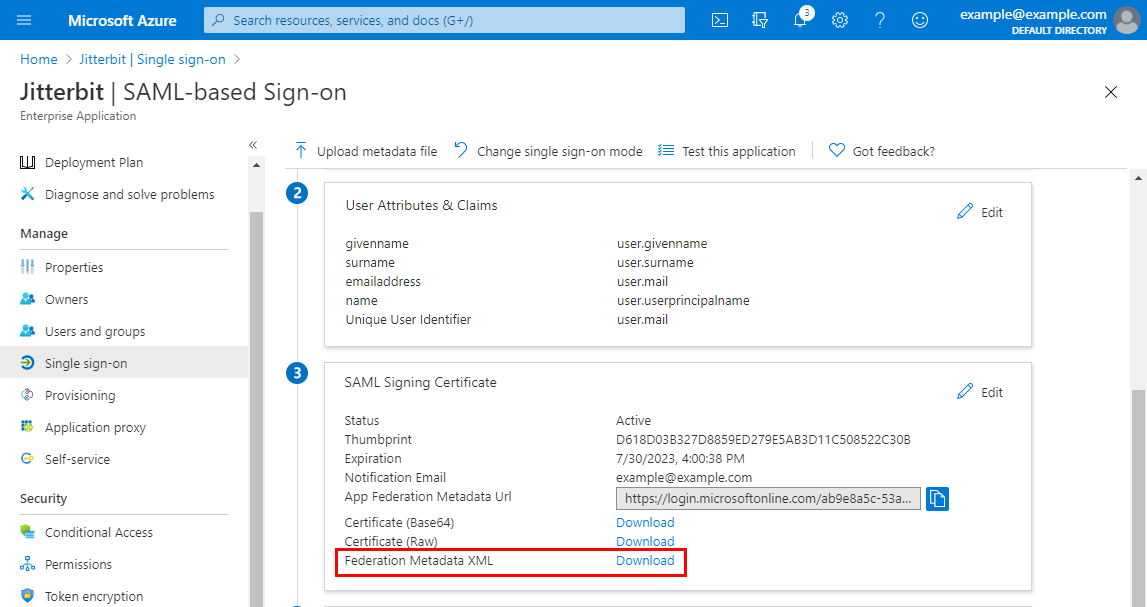
-
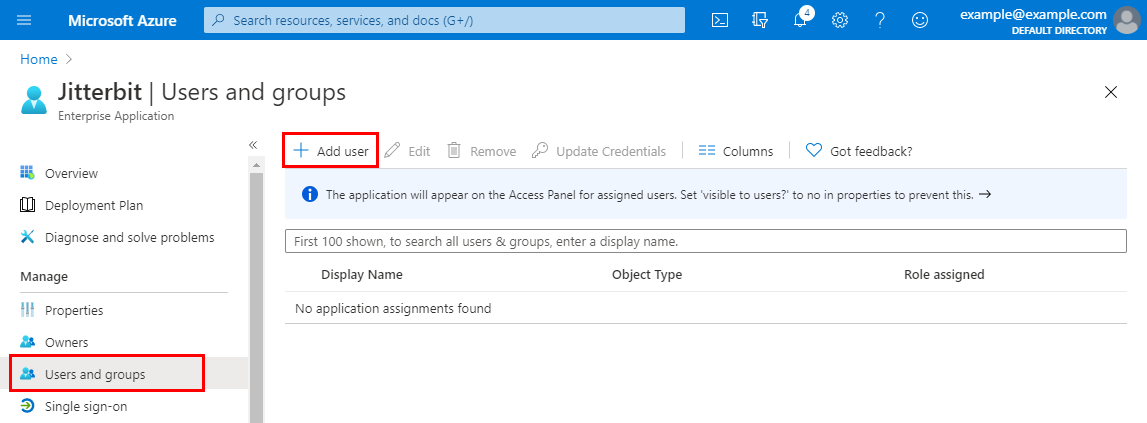
Under the Manage category on the left, select Users and groups.
-
For each user, click Add user and add their email address.
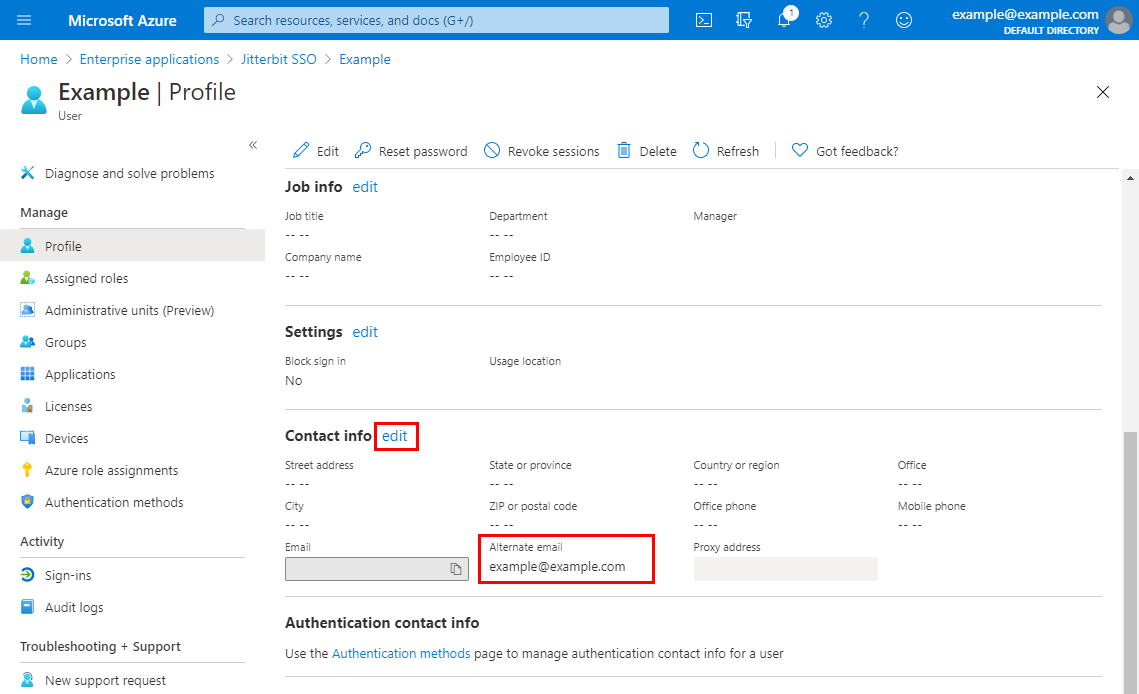
-
After adding each user, provide an Alternate email that matches the Harmony username. These users must be members of the Harmony organization.
-
To create the service provider metadata for the WMC and Studio clients, use the samples below, replacing
REGIONon the highlighted lines with your Harmony region's SAML redirect and callback URLs for the Jitterbit client application:WMC<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"/> </md:SPSSODescriptor> </md:EntityDescriptor>Studio<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml/login/studio/callback"/> </md:SPSSODescriptor> </md:EntityDescriptor> -
Use these metadata in the Service Provider Metadata field in the app's section of the Configure SSO SAML 2.0 drawer on the Management Console Organizations page. to configure SSO for SAML 2.0.
Salesforce
To get the SAML 2.0 identity and service provider metadata for Salesforce, log in to the Salesforce Classic UI as a Salesforce Admin, then follow these steps:
-
Navigate to Setup > Administer > Security Controls > Identity Provider.
-
In the section Identity Provider Setup, verify that you have a domain name configured and that Salesforce is enabled as an identity provider:
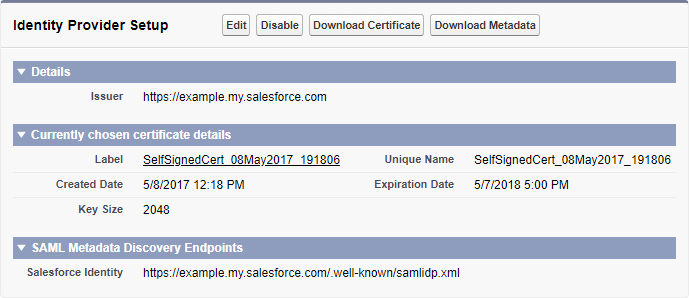
-
If you do not have a domain configured, click the link to Configure a Domain Name and follow the steps to set up a domain and deploy it to users. This automatically enables Salesforce as an identity provider.
-
If you have a domain configured but disabled as an identity provider, click the button Enable Identity Provider.
Tip
After making changes in Identity Provider Setup, you may need to refresh the page.
-
Do the following steps for two Jitterbit client applications, WMC, for access to the Harmony web applications via the Harmony portal, and Studio, for access to Design Studio:
Important
You must create both apps even if you don't intend to use Design Studio.
-
In the Service Providers section, click the link to create via Connected Apps, or navigate to Setup > Build > Create > Apps and click New under the Connected Apps section.
-
Set the following values:
-
Basic Information:
-
Connected App Name: Enter a name for the Jitterbit client application.
-
Set any other required fields.
-
-
Web App Settings:
-
Enable SAML: Enable this setting to reveal the Entity Id and ACS URL fields:
For WMC:
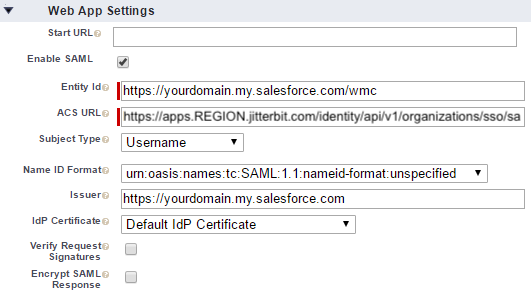
For Studio:
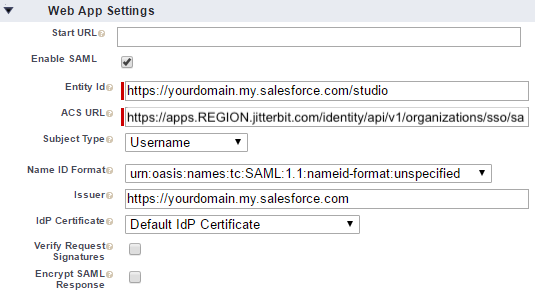
Set these fields as follows:
-
Entity Id: This must be unique per Harmony client.
Tip
Inspect the downloaded XML metadata file and find the
entityIDelement. This should match your Salesforce domain (https://yourdomain.my.salesforce.com/). To create a unique Entity Id per client, you can append/wmcor/studioto the default ID. -
ACS URL: Enter your Harmony region's redirect or callback URL for the Jitterbit client application.
-
-
-
-
Complete any other optional fields as desired, and click Save.
To assign profiles to the Connected Apps so that users have the appropriate permissions, follow these steps:
-
For each Connected App, click the Manage button, or navigate to Setup > Administer > Manage Apps > Connected Apps.
-
You must assign profiles for each Connected App. Do the following for each:
-
Under the Profiles section, click Manage Profiles.
-
On the Application Profile Assignment screen, select System Administrator. This provides access to the service provider.
Select any additional profiles associated with users using Harmony SSO.
-
When all desired profiles have been assigned, click Save.
-
-
The Harmony clients should now be listed under Manage Connected Apps. (You may not see the apps from the identity provider page listed under service providers.)
-
To create the service provider metadata for the WMC and Studio clients, use the samples below, replacing (on the highlighted lines)
ENTITY_IDwith the Salesforce Entity ID, andREGIONwith your Harmony region's SAML redirect and callback URL for the Jitterbit client application:WMC<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="ENTITY_ID"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"/> </md:SPSSODescriptor> </md:EntityDescriptor>Studio<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="ENTITY_ID"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml/login/studio/callback"/> </md:SPSSODescriptor> </md:EntityDescriptor>Tip
If you see the error No valid signing cert found, check that the identity provider metadata has a
KeyDescriptortag with the attributeuse="signing".
Okta
To get the SAML 2.0 identity and service provider metadata for Okta, log in to your Okta organization as a user with administrative privileges, then follow these steps:
-
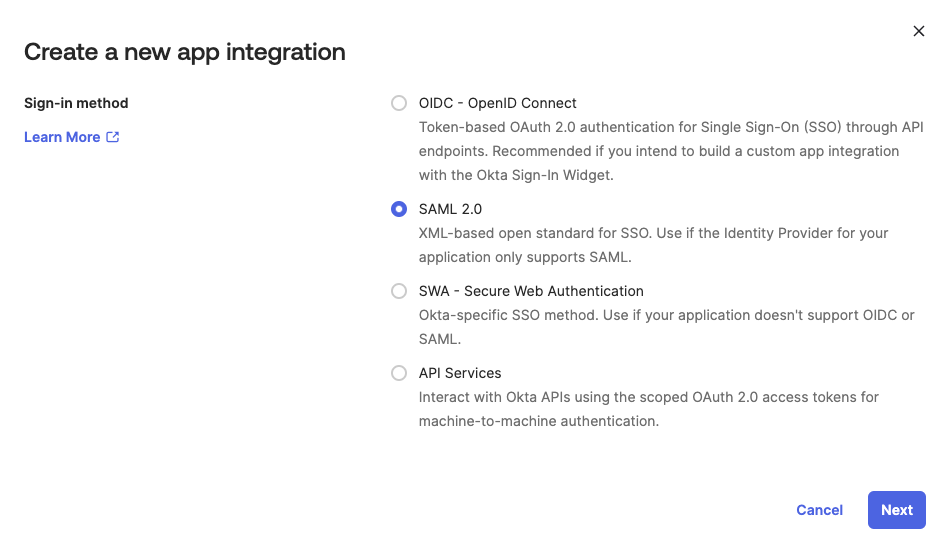
On the main menu, go to Applications > Applications, then click Create App Integration.
-
In the Create a new app integration window, select SAML 2.0 and click Next.
-
On the Create SAML Integration page, several steps walk you through configuring the new app.
-
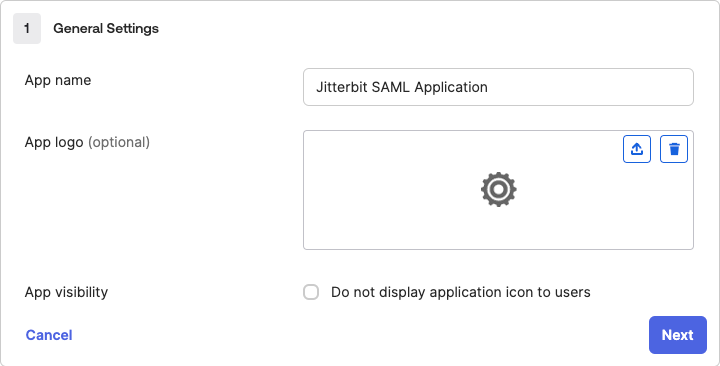
In step 1, General Settings, enter an App name, then click Next:
-
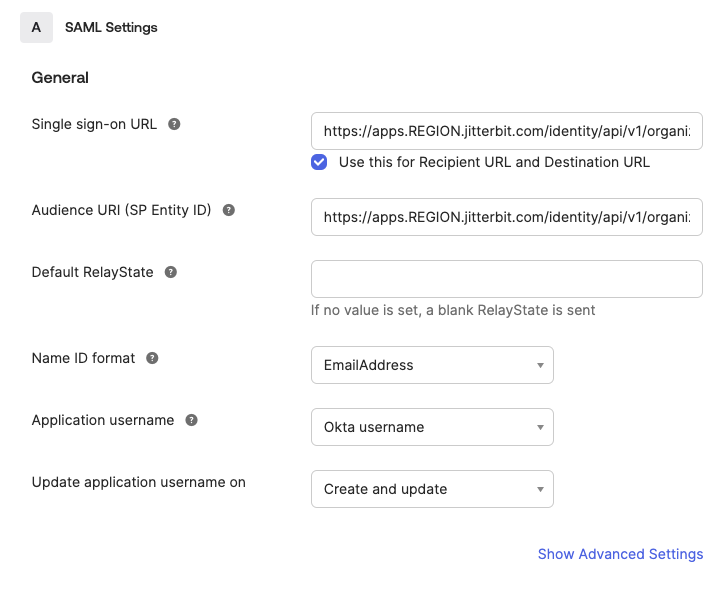
In step 2, Configure SAML, provide the following information under part A, SAML Settings:
-
Single sign on URL: Enter your Harmony region's SAML 2.0 redirect URL for the WMC Jitterbit client application.
-
Audience URI (SP Entity ID): Again, enter your Harmony region's SAML 2.0 redirect URL for the WMC Jitterbit client application.
-
Name ID format: Click the dropdown and choose the EmailAddress option. Leave the remaining fields with their default values.
-
-
Click Show Advanced Settings.
-
Under Other Requestable SSO URLs, click + Add Another. Enter your Harmony region's SAML 2.0 callback URL for the Studio Jitterbit client application. Leave the remaining fields with their default values.
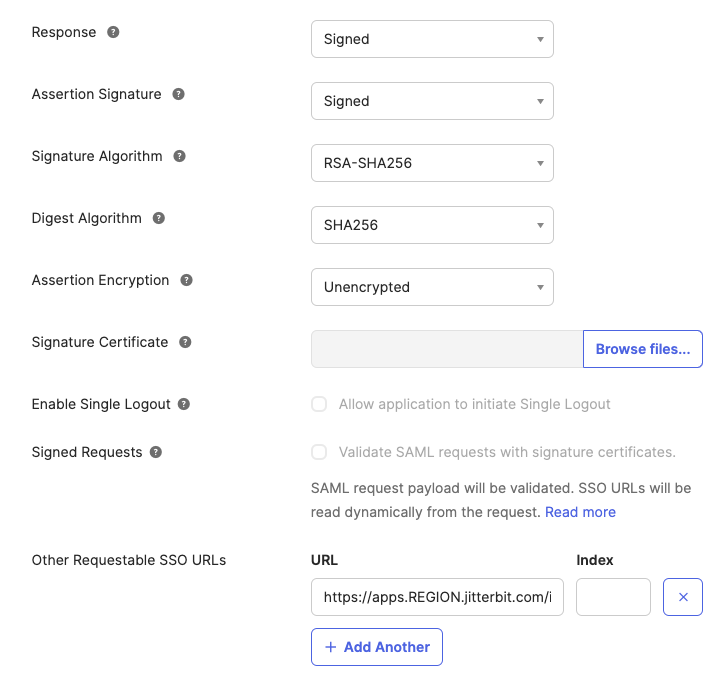
-
-
When finished, you can skip part B and click Next to continue.
-
Complete the last step, Feedback, then click Finish to finish creating the app.
To create the metadata for the Service Provider Metadata field in the app's section of the Configure SSO SAML 2.0 drawer on the Management Console Organizations page, follow these steps:
-
Go to the Sign On tab of your newly created application.
-
In the Actions column, select Actions > View IdP Metadata to download the metadata file:
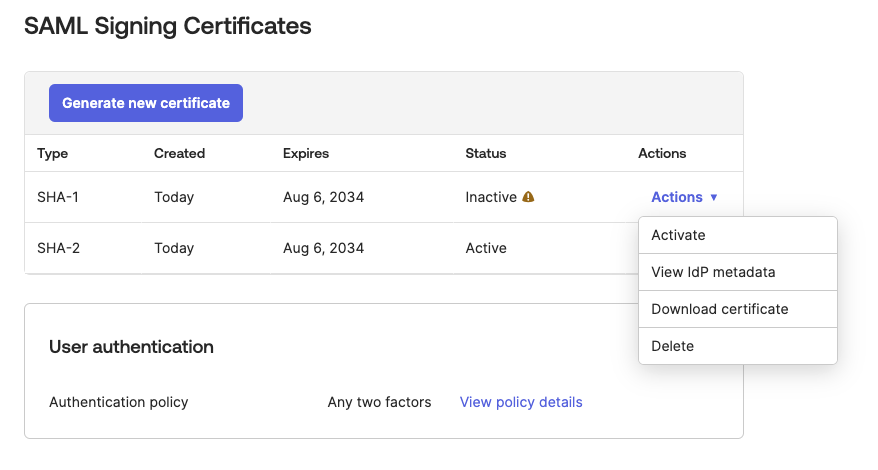
This example shows how the metadata file should look:
Example Identity Provider Metadata<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.okta.com/exknvfdjbL8smSRvK2p6"><md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate>MIIDqjCCApKgAwIBAgIGAWFj+QgOMA0GCSqGSIb3DQEBCwUAMIGVMQswCQYDVQQGEwJVUzETMBEG A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU MBIGA1UECwwLU1NPUHJvdmlkZXIxFjAUBgNVBAMMDWppdHRlcmJpdGJsdWUxHDAaBgkqhkiG9w0B CQEWDWluZm9Ab2t0YS5jb20wHhcNMTgwMjA1MDMxNzQwWhcNMjgwMjA1MDMxODQwWjCBlTELMAkG A1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lzY28xDTAL BgNVBAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRYwFAYDVQQDDA1qaXR0ZXJiaXRibHVl MRwwGgYJKoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB CgKCAQEAwRuDKQWs/uWFEulxYk1/V436/zhy/XxAL3swKUdfFlevC4XZcQtTdpspgwdt0TIgTpz1 dZGx5ystxz1slZ5e9jk20iHAsRuzKKeL657DDFHlG8Qg7HCg8B55TKKhTUsYQLikqeWx8R7F+rHh dG6eEJut4/CHOMlb/G4Ynrq8tpwlqVtaqLZrL2GPfEKUJVOvqxHeqVqmB7Pduh3E9/7rgEN6yXiL 6hISTRLIb13TGGyqpLPMRsgJnkMifQMI12OK0PQnFqRc2ES0JUnWhpv/WN4VYuvN3SgaIgE5VY86 C0J8IB6ljXx6uJj6EeC60KTmDUPtC1Au345jzBwY9yKLoQIDAQABMA0GCSqGSIb3DQEBCwUAA4IB AQAD7Ba6pwUUmxCtiqKE4E4JwMMCUrlHghL80Vru3SHWU3GdMEM9kVizVUcM57QzyIlwx8KdCXbB yfxo8Eh88mAYDRifLmeospLQvC5OhfF/5XKmsTa5JnF+bSB41iCZUsB88byLI1nARFZGznboQXK9 pT3egaEHsWffiIYR+Y2lcAW66OH6FEZ0lTy628q1LsuS/UruA3so+qFgPqTc0yiZEv65MZQWd1cg qRlLK1bcoR4d5Qfo0nWFDBXWqX4LX4c5xe7zh4wtbiG1i9Oh8qWJp8KUmgfSkQf79mUhib9YvzBE RdXU7eUS0/E3G21yLa9wQtHkEY3cIDs58AEIpuR0</ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://jitterbitblue.okta.com/app/jitterbitorg316974_jitterbitsamlapplication_1/exknvfdjbL8smSRvK2p6/sso/saml"/><md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://jitterbitblue.okta.com/app/jitterbitorg316974_jitterbitsamlapplication_1/exknvfdjbL8smSRvK2p6/sso/saml"/></md:IDPSSODescriptor></md:EntityDescriptor>
To assign users to the Jitterbit SAML application within Okta, follow these steps:
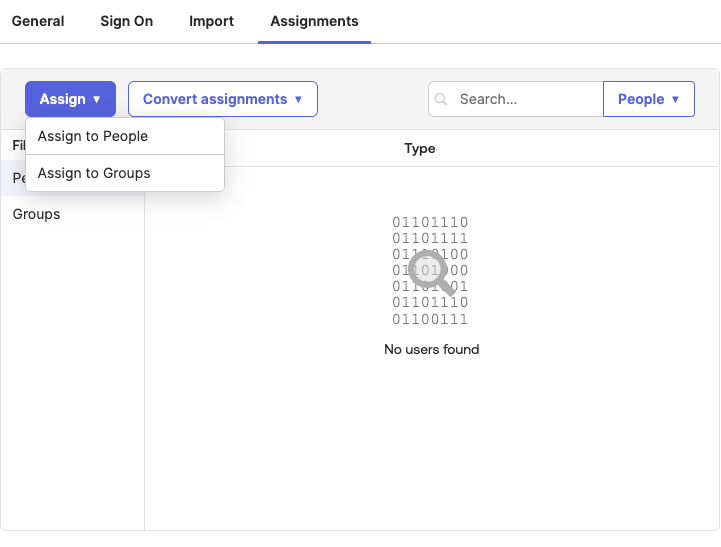
-
Go to the Assignments tab of your newly created Jitterbit application.
-
For each user that must log in to Harmony via Okta, click the Assign dropdown, select Assign to People, then assign them.
-
When finished, click Done.
-
To create the service provider metadata for the WMC and Studio clients, use the samples below, replacing
REGIONwith the SAML URL for the Harmony region on the highlighted lines:WMC<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"/> </md:SPSSODescriptor> </md:EntityDescriptor>Studio<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://apps.REGION.jitterbit.com/identity/api/v1/organizations/sso/saml/login/studio/callback"/> </md:SPSSODescriptor> </md:EntityDescriptor>Tip
If you see the error No valid signing cert found, check that the identity provider metadata has a
KeyDescriptortag with the attributeuse="signing".