Sessions in Jitterbit App Builder
All interactions with App Builder occur within the context of a session. A session is created when a user first visits App Builder. Subsequent requests from the same user are associated with the session.
If you are looking to set a timeout based on user inactivity for security purposes, this can be accomplished by setting an Authentication Expiry value. See the Authentication + Session Timeout section of this article for more information.
Tracking
App Builder tracks sessions by assigning each individual browser a unique identifier. The identifier is stored in an in-memory cookie. As such, closing (all instances of) the browser effectively terminates the session. The cookie is marked HttpOnly. If the browser is connected to the server using HTTPS, the cookie is also marked as Secure.
For maximum compatibility across data provider implementations, the session identifier takes the form of UUID. Specifically, it's a version 4 UUID, generated using a cryptographically random number generator. UUIDs are composed of 128 bits. However, 6 bits are reserved to identify the version. This provides a total of 122 bits of randomness, which should be sufficiently long as to be unguessable.
Development
Developers can access the current session identifier using the session() mvSQL function. This is available regardless of whether an event executes in foreground or background. Note, however, that scheduled events are assigned a transient session identifier. The transient session identifier is not associated with a user session and changes each time the scheduled event executes.
Session identifiers can be stored in columns of type "Unique ID".
Authentication + session timeout
Sessions themselves will not timeout. However, security administrators can set the authentication expiry which provides control over session timeout. The authentication expiry defines the lifetime for security tokens. When a user signs in, he or she is granted a security token. The security token itself has a lifetime with a sliding window: App Builder will issue a new token if the user interacts with App Builder more than halfway through the expiration window.
By default, the security token has a lifetime of 2 weeks. To set the authentication expiry:
- Log into App Builder as an administrator.
- Navigate to the IDE.
- Click the Security Providers button.
- In the Configuration panel, click the Edit button.
-
Provide a value for the Authentication Expiry.
- The security token lifetime is measured in minutes.
-
Click the Save button.
Note
The security token lifetime only applies to newly issued security tokens.
How to configure sessions
By default, App Builder persists session information to the database. Administrators can view sessions and forcibly sign out user sessions. Tracking sessions guards against certain vulnerabilities, such as cookie-replay attacks. This article describes the configurable session storage policies.
To configure sessions
- Navigate to the IDE
- In the Connect panel, click the Security Providers button
-
The following options can be found in the Configuration panel under Sessions:
-
Session Storage = Determines when sessions are stored. Options:
- Authenticated = Stores only authenticated sessions.
- Nonpersistent = Sessions are not stored. Matches the legacy behavior.
- Persistent = Stores all anonymous and authenticated sessions.
- Sign Out = Stores only signed-out sessions.
-
Anonymous Expiry = Numeric value (seconds) that determines how long anonymous sessions are stored.
- Max Concurrent = Numeric value (count) that specifies the maximum number of concurrent sessions a User can have at one time.
-
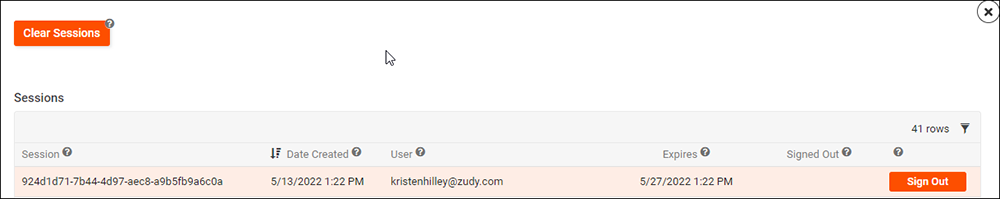
To manage sessions
- Navigate to the IDE
- In the Runtime panel, click the User Management button
- In the Users panel, click the More button and choose Sessions
-
From here, you can view existing sessions, sign out individual sessions, or clear all sessions (including your own).